SharePoint Online and OneDrive Setup for Enterprise Search (Indexed and Live Search)
This page is for the Sharepoint OneDrive NG (Next Gen) connector for SharePoint Online and OneDrive and it can only be configured within the new enterprise search configuration experience explained below.
Currently, the new experience is only available for SharePoint Online. For SharePoint Server(On-Prem), please reach out to your customer success team.
Please visit this documentation to learn more about Next Gen and Classic connectors.
System Overview
Microsoft 365’s SharePoint Online is your organization’s hub for sites, pages, and document libraries. From an enterprise-search perspective, it’s a primary repository of institutional knowledge and files that can be indexed to make content easily discoverable across the organization with permissions intact.
OneDrive for Business is each user’s personal file store connected to their organization account, where they can store, access, and sync their individual work files across multiple devices. It is private by default, and files are only accessible to others if the user explicitly chooses to share them.
Moveworks supports both - indexing content from SharePoint sites ensuring users can search pages and documents which they are authorized to view as well as live search over SharePoint Online sites that the user has access to serve content beyond ingestion limits.
OneDrive is currently only supported via live search (with user consent); Moveworks does not index OneDrive data.
Authentication
Authentication is accomplished by creating and registering an Azure App Registration for each of the following approaches.
- Indexing (SharePoint Online only)
- Uses app-only access with certificate-based OAuth (JWT bearer) through an Azure App Registration.
- You upload the cert’s public half to the app, compute the x5t (SHA-256) thumbprint, and provide the private key (PEM) to Moveworks.
- Recommended permission model:
Sites.Read.All- Enables full discovery, All Sites/All except selected options in Content Selection, and near-real-time incremental ingestion (webhook-driven).
- Lesser-privilege alternative:
Sites.Selected. Choose only if your security policy strictly requires it.- Extra admin steps required: you must grant site-specific access to the app for every site to be indexed and ensure the app can resolve site group visibility for all groups within each permissioned site (so ACLs can be read).
- Content Selection UI impact:
All SitesandAll except selectedare not available; you can only chooseOnly selected sites. - Ingestion frequency impact: Webhooks are not available; ingestions will run on a daily schedule (not the typical ~15-minute incremental SLA).
- Live Search (SharePoint Online & OneDrive)
- Uses delegated OAuth with a separate Azure App Registration and client secret.
- End users sign in and consent the first time; Moveworks then searches only the files they can access in SharePoint and OneDrive.
- No enterprise-wide indexing of OneDrive content occurs.
A single unified connector in Moveworks collects both sets of credentials—one block for Indexing (certificate/JWT) and another for Live Search (delegated).
Permissions Enforcement
Moveworks honors native Microsoft 365 ACLs at all times.
- Indexing: Item- and site-level permissions (including group membership) are captured and enforced at query time—users only see results they’re allowed to view.
- Live Search: Results are retrieved on behalf of the signed-in user using their delegated token, so source-system permissions are inherently enforced.
API Usage
- Moveworks uses the standard Graph API v1.0 and SharePoint REST API to fetch data from SharePoint Online and OneDrive. We use application permissions with admin-granted access for indexing content and delegated permissions for live search.
Content Types
Indexing (SharePoint Online)
- Pages (modern site pages, classic wiki pages and classic publishing pages).
- Documents stored in SharePoint document libraries (including common attachments).
- Supported file formats: doc, docx, pdf, ppt, pptx, txt, html, aspx(pages)
Live Search (SharePoint Online & OneDrive)
- On-demand results from the signed-in user’s accessible SharePoint sites/libraries and their OneDrive files/folders. It includes Pages, Documents, Lists etc.
- Not indexed into the enterprise corpus; fetched at query time after user consent.
Coverage & Freshness
Moveworks delivers comprehensive coverage—content, metadata, identity, and permissions—and uses incremental updates for indexed content.
- With
Sites.Read.AllandFiles.Read.All, webhooks allow near-real-time incremental updates. - With
Sites.Selected, updates are performed on a daily schedule due to the webhook limitations.
Access Requirements
Pre-requisites
Before you get started, make sure you have everything you need:
- Admin roles
- Global Admin permissions to create App registrations, upload certificates, and grant admin consent.
- SharePoint Admin permissions to identify your tenant domain(s) and (if using Sites.Selected) grant per-site permissions.
- Environment details
- Your SharePoint tenant domain(s), e.g., contoso (and contoso-eu, contoso-apc if applicable).
- Cloud environment: Commercial or GOV L4.
- Tools (recommended)
- PowerShell (Windows) with certificate cmdlets, or OpenSSL (macOS/Linux/Windows).
- Openssl is installed by default on OS X terminals
- PnP PowerShell if you’ll grant
Sites.Selectedper-site access via cmdlets.
- PowerShell (Windows) with certificate cmdlets, or OpenSSL (macOS/Linux/Windows).
Understanding Permissions Scopes required for Enterprise Search
SharePoint Indexing
Microsoft Graph API Group
- Sites.Read.All - Application Permission which provides access to read all Sharepoint Site Content across all Sites. Moveworks requires this access to ingest Files from all Sites.
Note : If your organisation does not want to provide access to All sites, you can instead provide Sites.Selected- Sites.Selected - Application Permission which is an alternate option allows you to narrow down Moveworks search to content from only SPECIFIC sub sites in the tenant.
This requires additional setup, Please ensure these instructions are followed if Sites.Selected Permission is being provided. Note: With Sites.Selected, Files.Read.All is no longer required
- Sites.Selected - Application Permission which is an alternate option allows you to narrow down Moveworks search to content from only SPECIFIC sub sites in the tenant.
- Files.Read.All - Application Permission which is provides access to read File content inside a Sharepoint Site. Moveworks requires this access to ingest the Files as well as register webhooks to conduct incremental sync of data.
- Group.Read.All - Application Permission which provides access to read Microsoft AD Group details to the Files in the Sharepoint Site. Moveworks requires this access to ingest Microsoft AD Groups for respecting Permissions
- User.Read.All - Application Permission which allows access to read all user information in the tenant. Moveworks requires this access to ingest user details from the Azure tenant which will be used to respect permissions
SharePoint API Group
- Sites.Read.All - Application Permission which provides access to read all Sharepoint Site Content across all Sites. Moveworks requires this access to ingest Files from all Sites.
Note : If your organisation does not want to provide access to All sites, you can instead provide Sites.Selected- Sites.Selected - Application Permission which is an alternate option allows you to narrow down Moveworks search to content from only SPECIFIC sub sites in the tenant.
This requires additional setup, Please ensure these instructions are followed if Sites.Selected Permission is being provided.
- Sites.Selected - Application Permission which is an alternate option allows you to narrow down Moveworks search to content from only SPECIFIC sub sites in the tenant.
The Sites.Read.All or Sites.Selected Permission needs to be provided to Both API Groups.
In this approach we will maintain a single Azure Application which will provide access to both SharePoint and Microsoft Graph APIs listed above.
SharePoint and OneDrive Live Search
Microsoft Graph API Group
- Files.Read.All: lets Moveworks read files the user already has access to in OneDrive and SharePoint document libraries, so it can surface relevant results.
- Sites.Read.All: lets Moveworks read site pages and list items the user can access in SharePoint Online.
- User.Read: identifies the signed-in user.
- offline_access: allows Moveworks to store a refresh token so the user doesn’t have to re-consent every time they search.
In this approach we will again maintain a single Azure Application which will provide access to Microsoft Graph APIs listed above but will be a different application than the Indexed one.
Instructions for SharePoint Indexing -App-only with certificate/JWT
1. Register a new App
-
Sign in to the Azure portal.
-
Select Microsoft Entra ID > Manage > App registrations > New registration.
-
On the Register an application page, register an app with the following details
Field Value Name MoveworksSupported account types Accounts in this organizational directory only (Single tenant) Redirect URI Leave this field empty 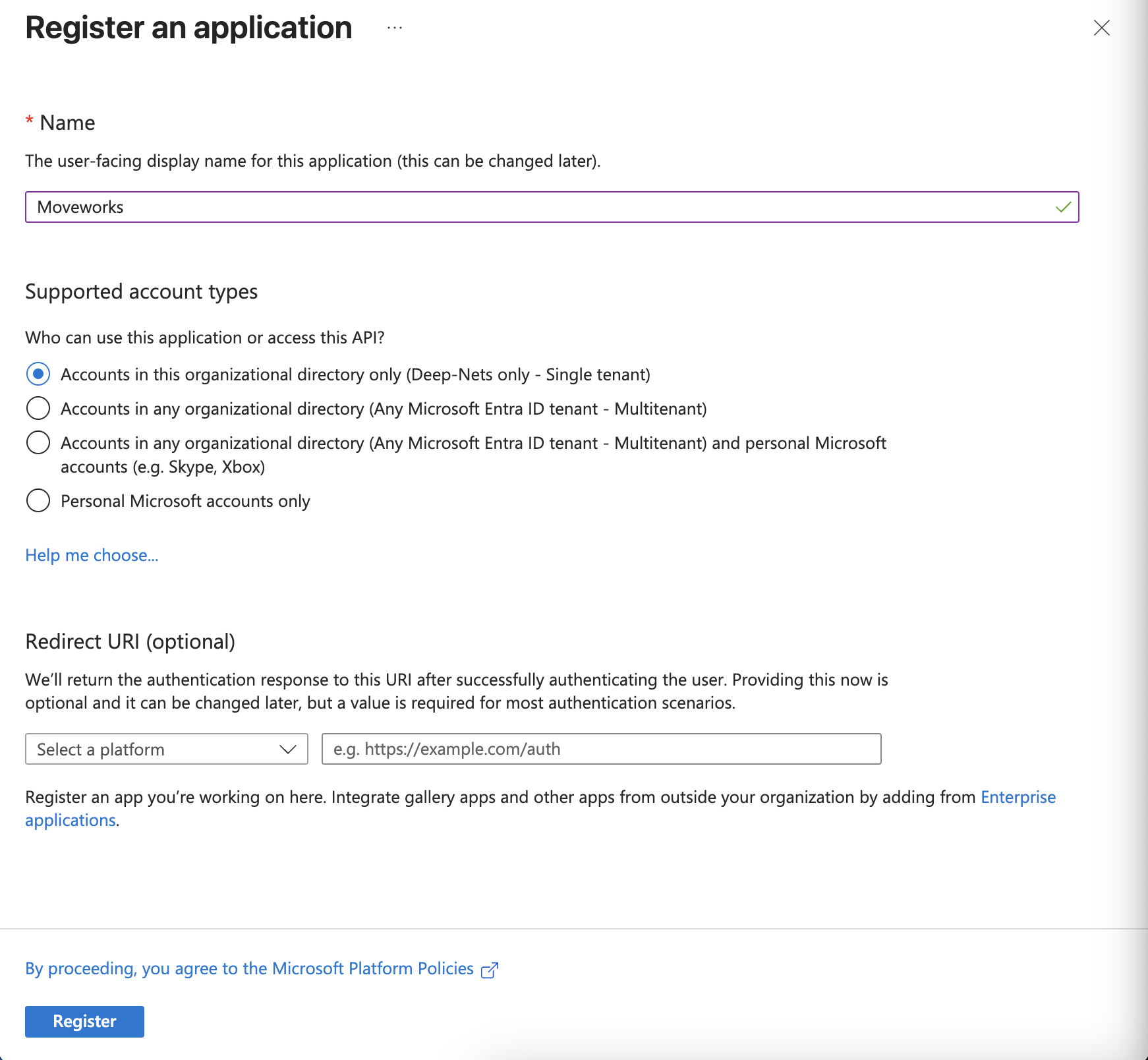
-
From the overview page, note down the following values:
- Directory (tenant) ID
- Application (client) ID
2. Add Application API permissions & grant Admin consent
-
Open the App Registration you created above and click on Manage > API Permissions.
-
Click Add a permission.
-
This will open a panel on the right side:
-
Select Microsoft Graph.
-
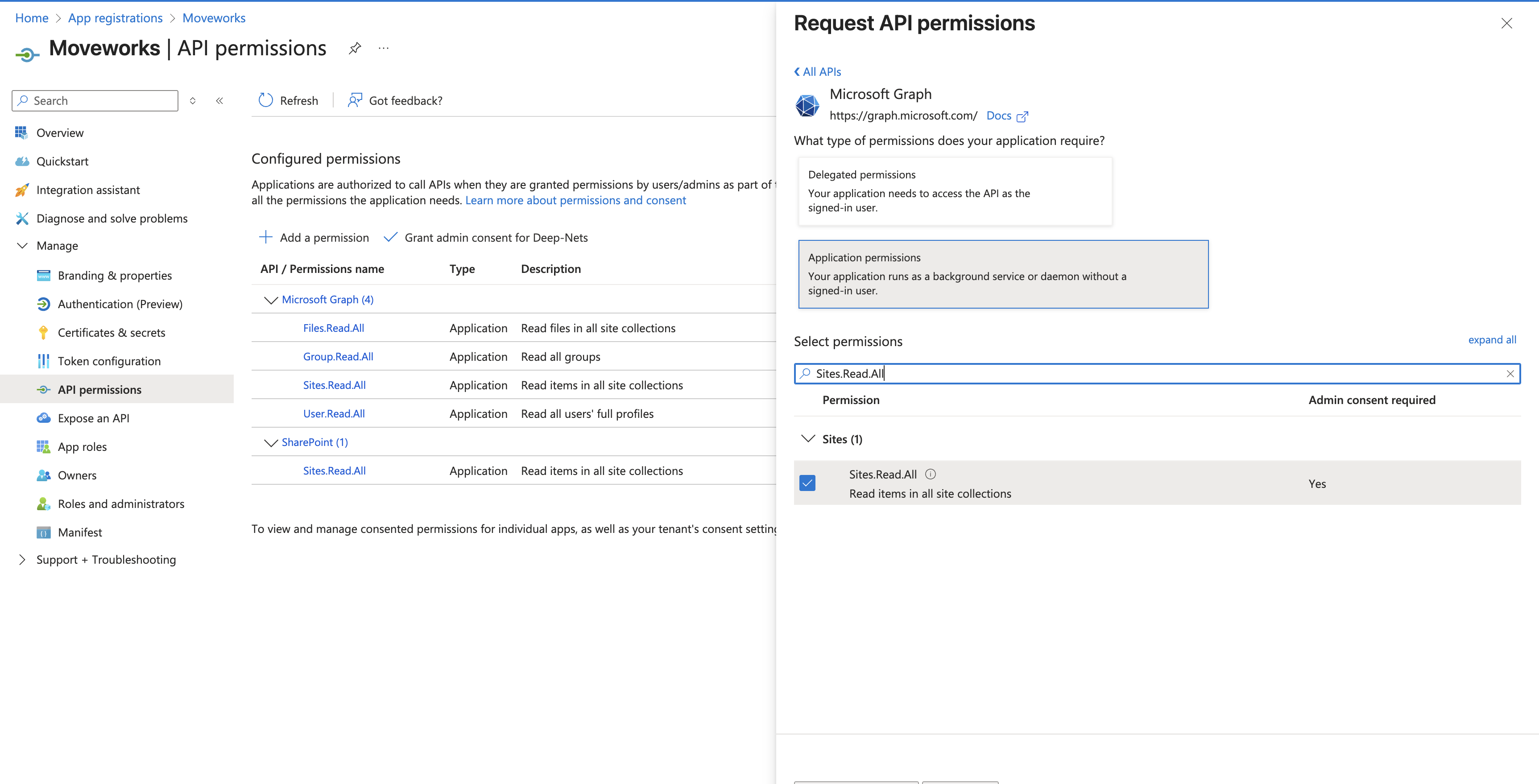
Choose Application permissions :
-
A search bar will appear:
-
Search for the permissions you need to grant(noted above) and check the box for each:
-
Once they’ve all been checked, click Add permissions
-
Repeat the steps again by clicking on Add a permission button and selecting SharePoint.
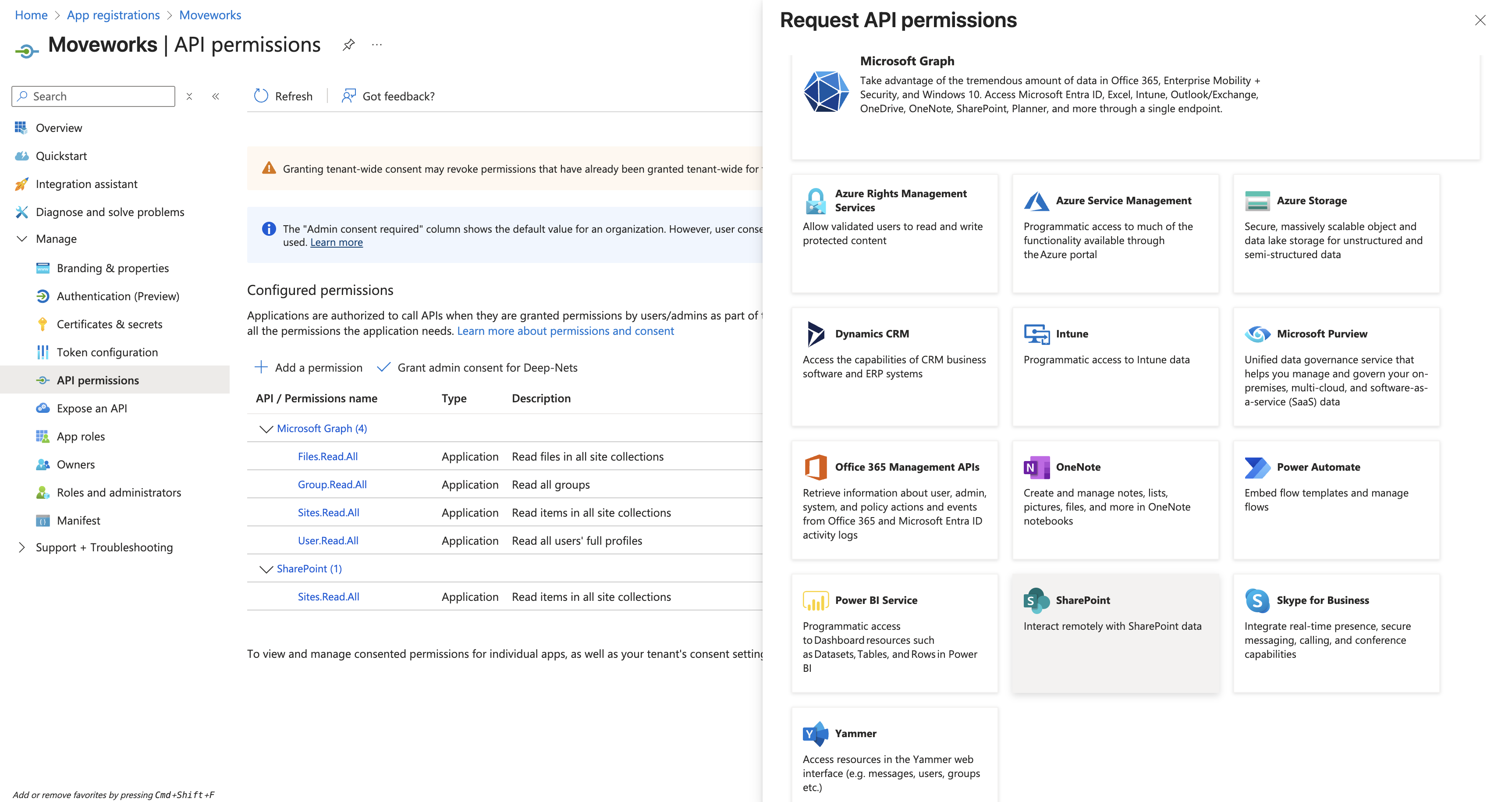
-
Similar to the previous steps, select Application permissions.
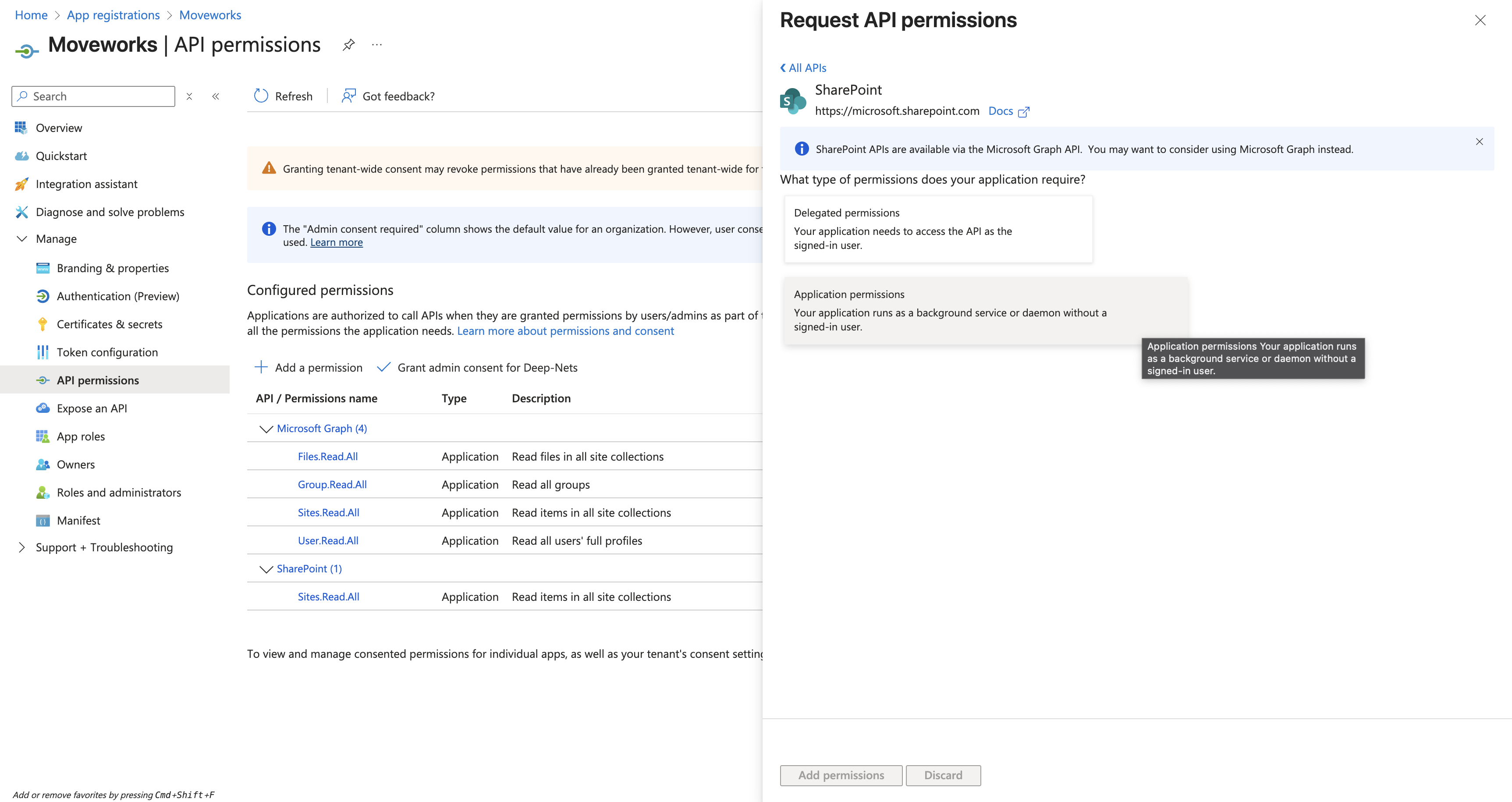
-
Select either Sites.Read.All or Sites.Selected based on your requirements (noted above) and click on Add permissions after selecting all scopes.
-
You’ll now see all the newly added permissions will have a status of “Not granted for” your organization.
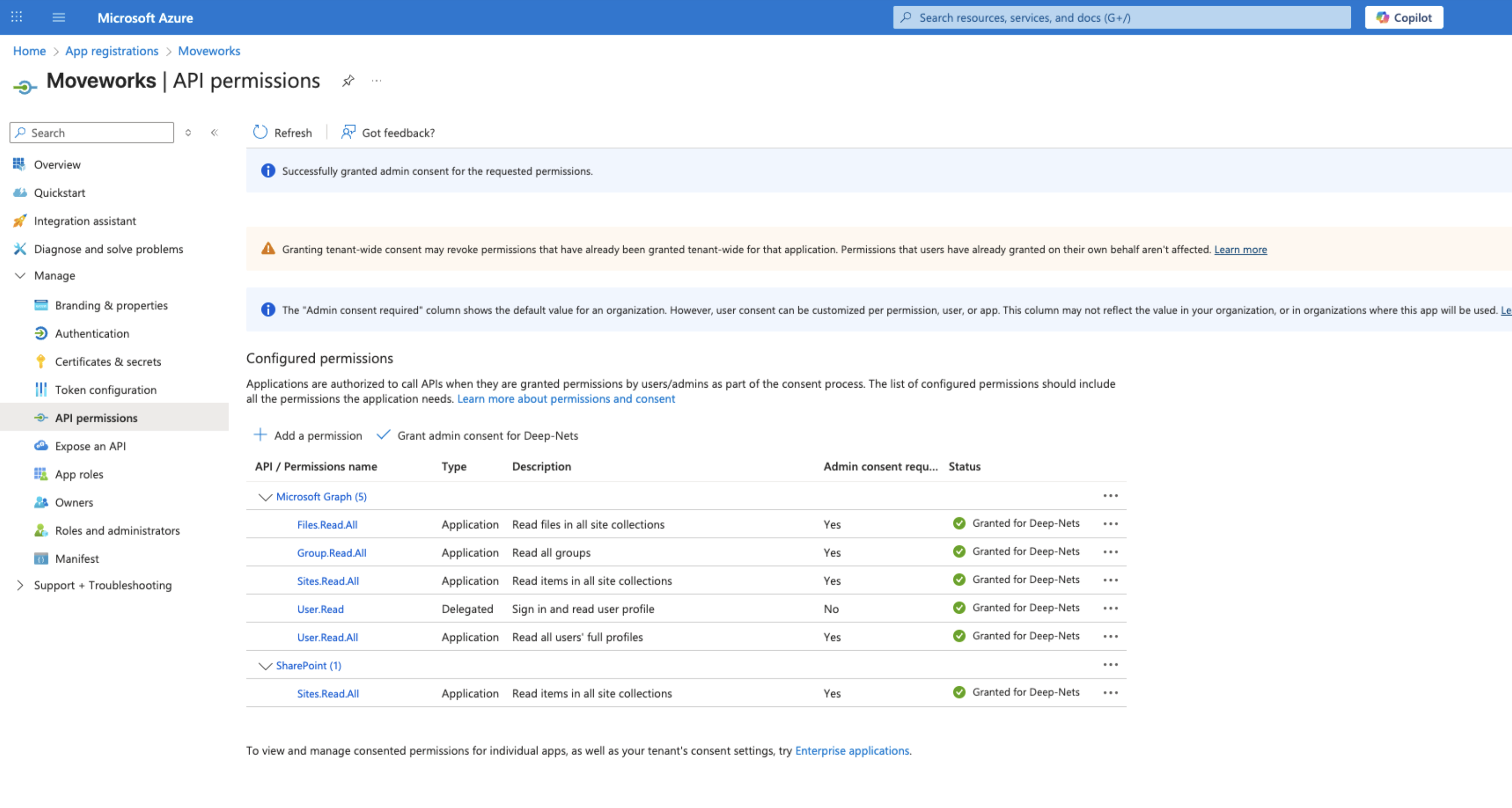
-
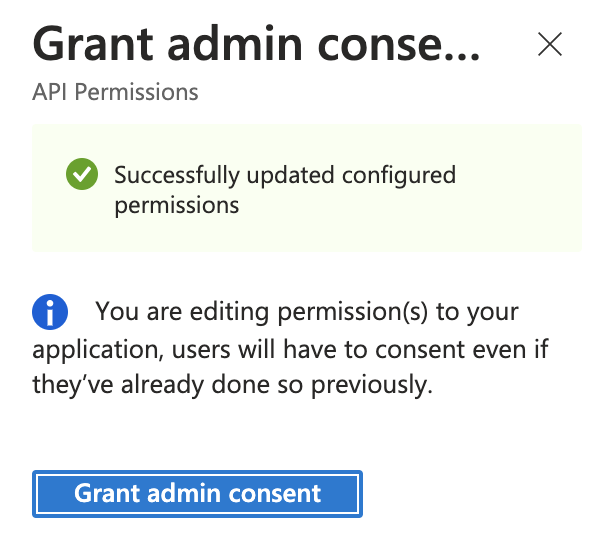
To complete the process, click Grant admin consent for your organization

-
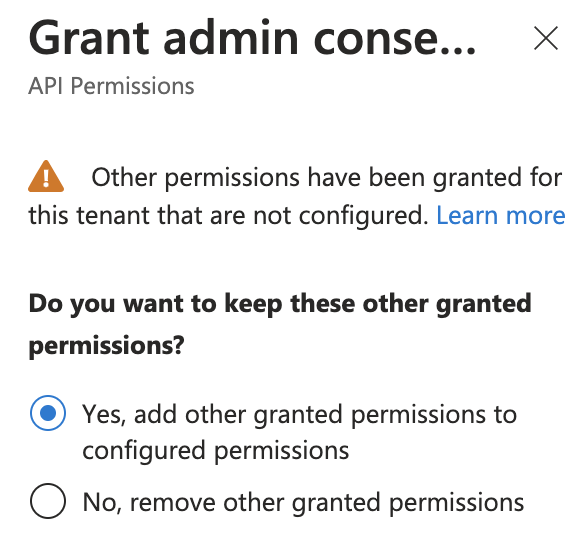
If this panel appears, click Yes, add other granted permissions to configured permissions then Save and continue, then Grant admin consent, and then Yes.
-
You will see green checkmarks on the newly added permissions if this was successful.
3. Generate a self-signed certificate and private key
You need:
- Public certificate (.cer) — upload to the app.
- Private key (privateKey.pem) — uploaded later in Moveworks.
Windows (PowerShell)
- Create a 2048-bit RSA, SHA-256 self-signed cert (exportable) with 2-year validity (replace the CertStoreLocation with your desired location)
$cert = New-SelfSignedCertificate ` -Subject "CN=Moveworks" ` -CertStoreLocation "C:\path\to\your\folder" ` -KeyAlgorithm RSA -KeyLength 2048 -HashAlgorithm SHA256 ` -KeyExportPolicy Exportable -KeySpec Signature ` -NotAfter (Get-Date).AddYears(2)
- Export the .pfx (choose a password) and .cer
$pwd = Read-Host -AsSecureString "Enter PFX password" Export-PfxCertificate -Cert "C:\path\to\your\file\$($cert.Thumbprint)" ` -FilePath ".\Moveworks.pfx" -Password $pwd Export-Certificate -Cert "C:\path\to\your\file\$($cert.Thumbprint)" ` -FilePath ".\certificate.cer"
- Export the private key (PEM) from Moveworks.pfx
openssl pkcs12 -in "C:\path\to\your\file\Moveworks.pfx" -nocerts -nodes -out "C:\path\to\output\file\privateKey.pem"
macOS/Linux (OpenSSL)
- Generate Private key + self-signed cert with 2 years validity
openssl req -x509 -newkey rsa:2048 -nodes \ -keyout privateKey.pem -out certificate.cer \ -days 730 -subj "/CN=Moveworks"
Verify that both certificate.cer and privateKey.pem are generated successfully in the desired location. Open each file, and ensure the files conform to the following formats:
- The certificate file must start with
BEGIN CERTIFICATEand end withEND CERTIFICATE - The private key should begin with
BEGIN PRIVATE KEYand end withEND PRIVATE KEY.- It must not include
RSAin the headers, nor be encrypted.
- It must not include
Store the private key in a safe storage since this will be used later to create the connector in Moveworks
4. Bind the cert to the app
- Navigate to the App you created above -> Certifications & secrets -> Certificates -> Upload certificate -> upload the
certificate.cerfile.
5. Compute x5t (SHA-256)
Windows (PowerShell)
$certPath = "path\to\your\certificate.cer"
$cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2($certPath)
$sha256 = [System.Security.Cryptography.HashAlgorithm]::Create("SHA256")
$hash = $sha256.ComputeHash($cert.RawData)
$x5t = [Convert]::ToBase64String($hash) -replace '\+','-' -replace '/','_' -replace '='
Write-Output $x5tmacOS/Linux (OpenSSL)
openssl x509 -in certificate.cer -outform der \
| openssl dgst -sha256 -binary \
| openssl base64 -A \
| tr '+/' '-_' | tr -d '='- Note down the x5t token value from the terminal output
Instructions for SharePoint and OneDrive Live Search-Delegated with client secret
1. Register a new App
-
Sign in to the Azure portal.
-
Select Microsoft Entra ID > Manage > App registrations > New registration.
-
On the Register an application page, register an app with the following details
Field Value Name Moveworks - Live SearchSupported account types Accounts in this organizational directory only (Single tenant) Redirect URI Web -> https://{org}.moveworks.com/auth/oauthCallback
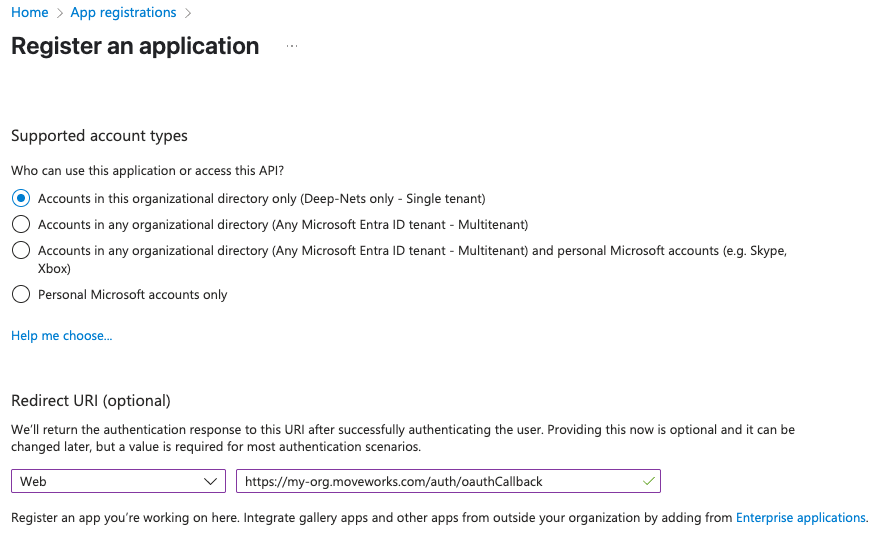
Note:
Ensure the Redirect URI is a Web application, and when specifying the Redirect URI, include your specific sub-domain for MyMoveworks.
https://{org}.moveworks.com/auth/oauthCallback— for US orgsMake sure to replace the
{org}with your specific sub-domain.
If you have a sandbox MyMoveworks environment, please configure an additional URL for that too:
-
On the Home page of the Application you just created, click on the Redirect URIs link
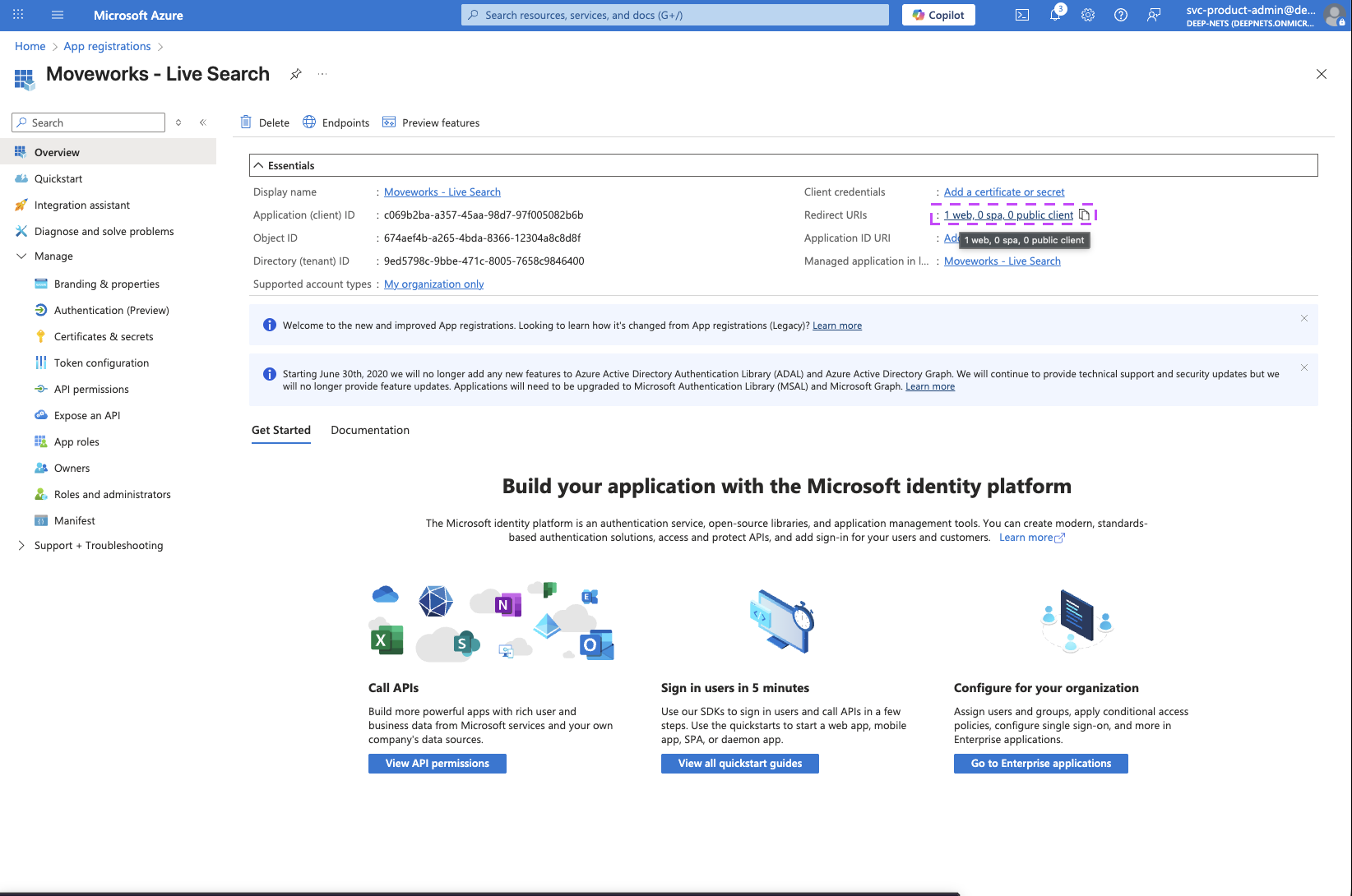
-
On the page that opens, click on the Add Redirect URI button to add an additional URI
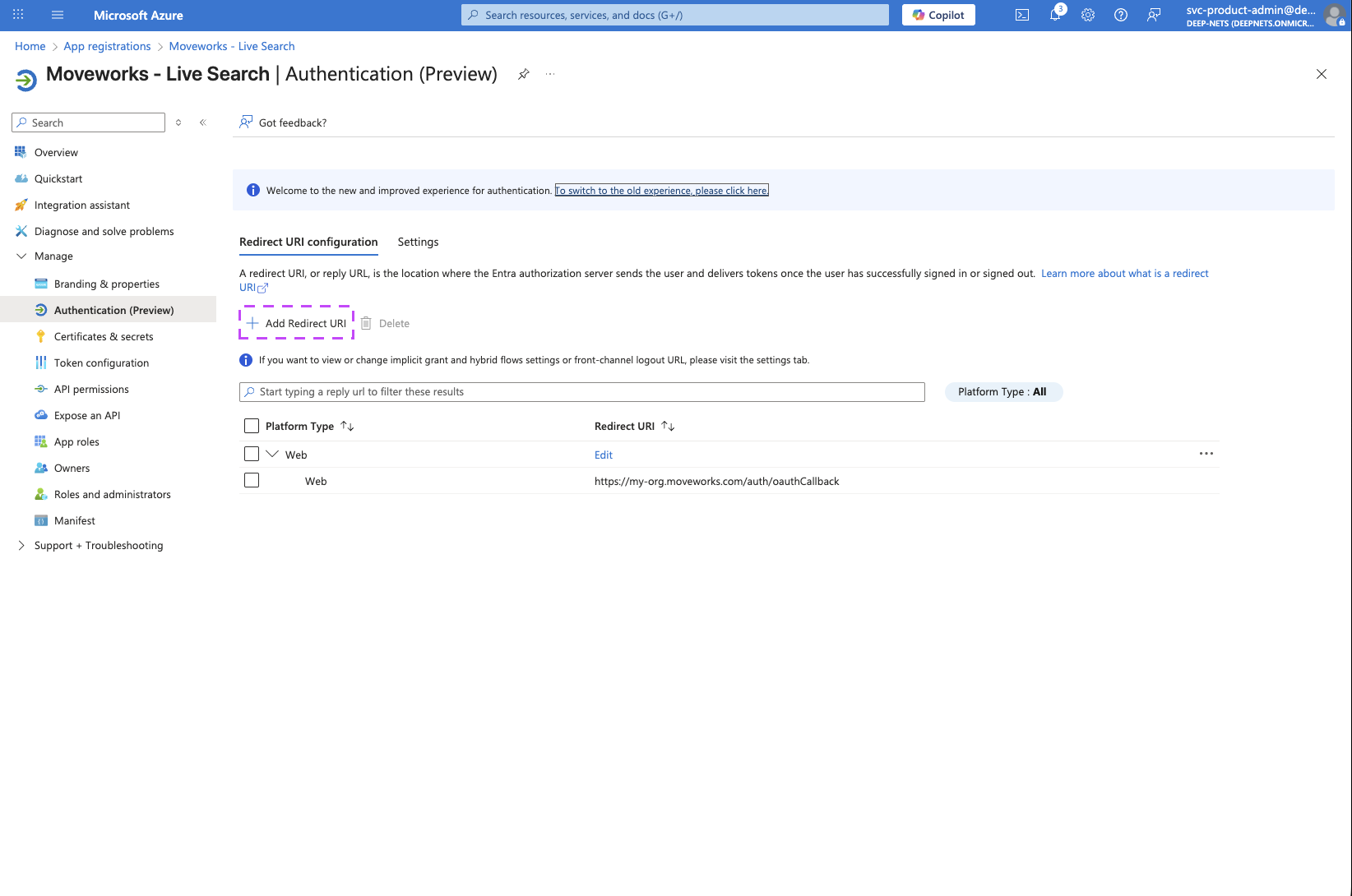
-
Select Web
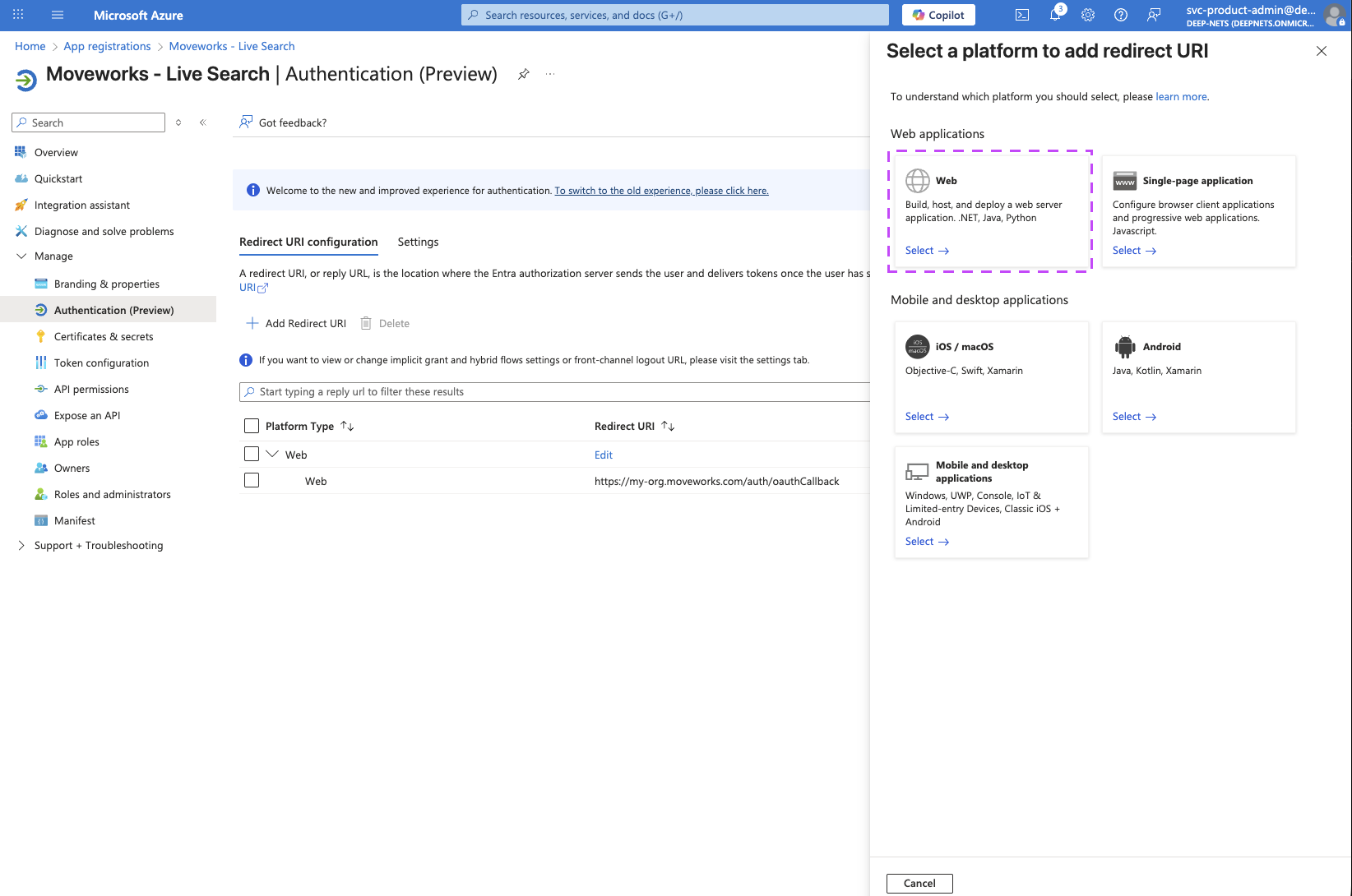
-
Enter the URL for your sandbox MyMoveworks environment and click on Configure.
https://{org}-sandbox.moveworks.com/auth/oauthCallback— for US orgs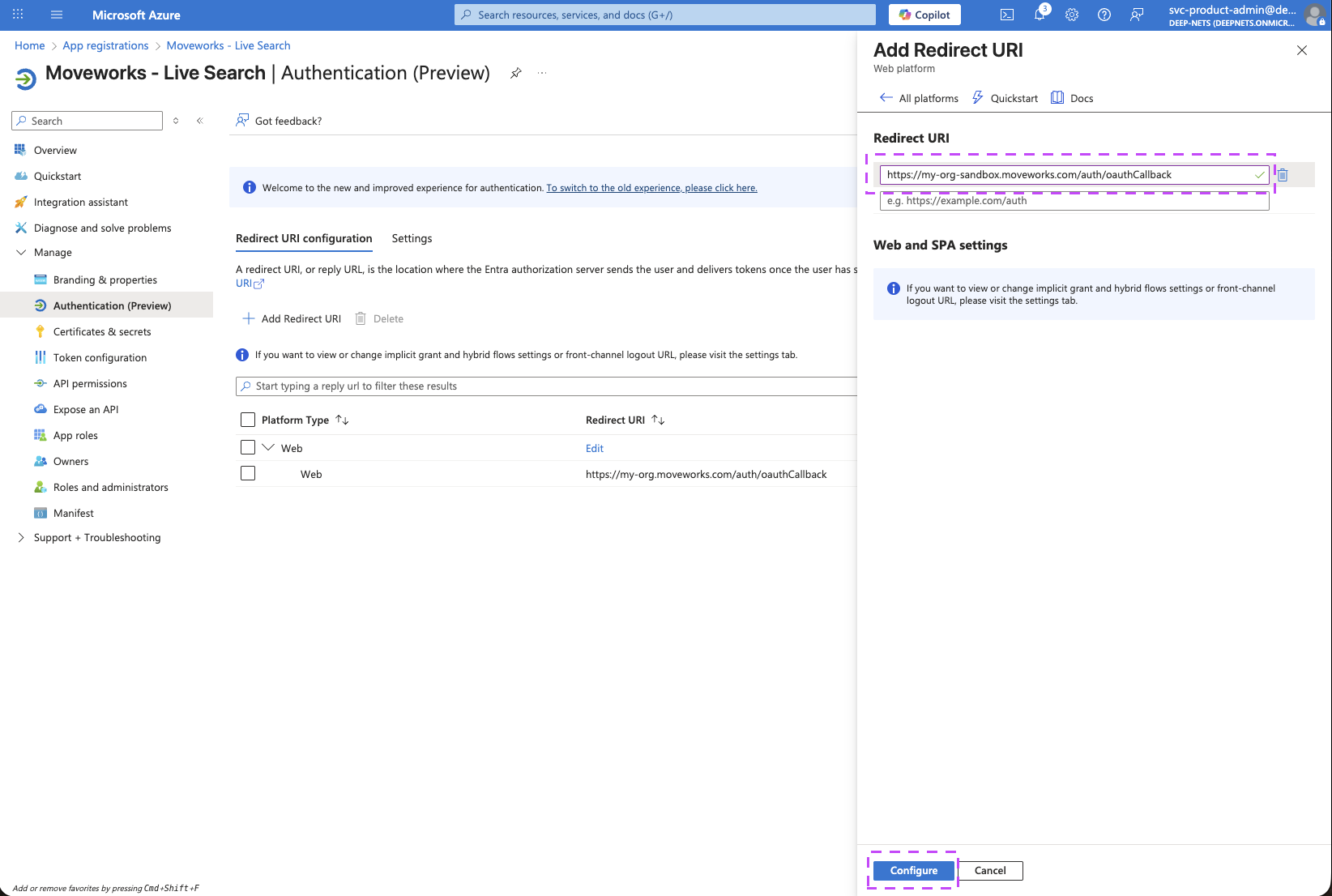
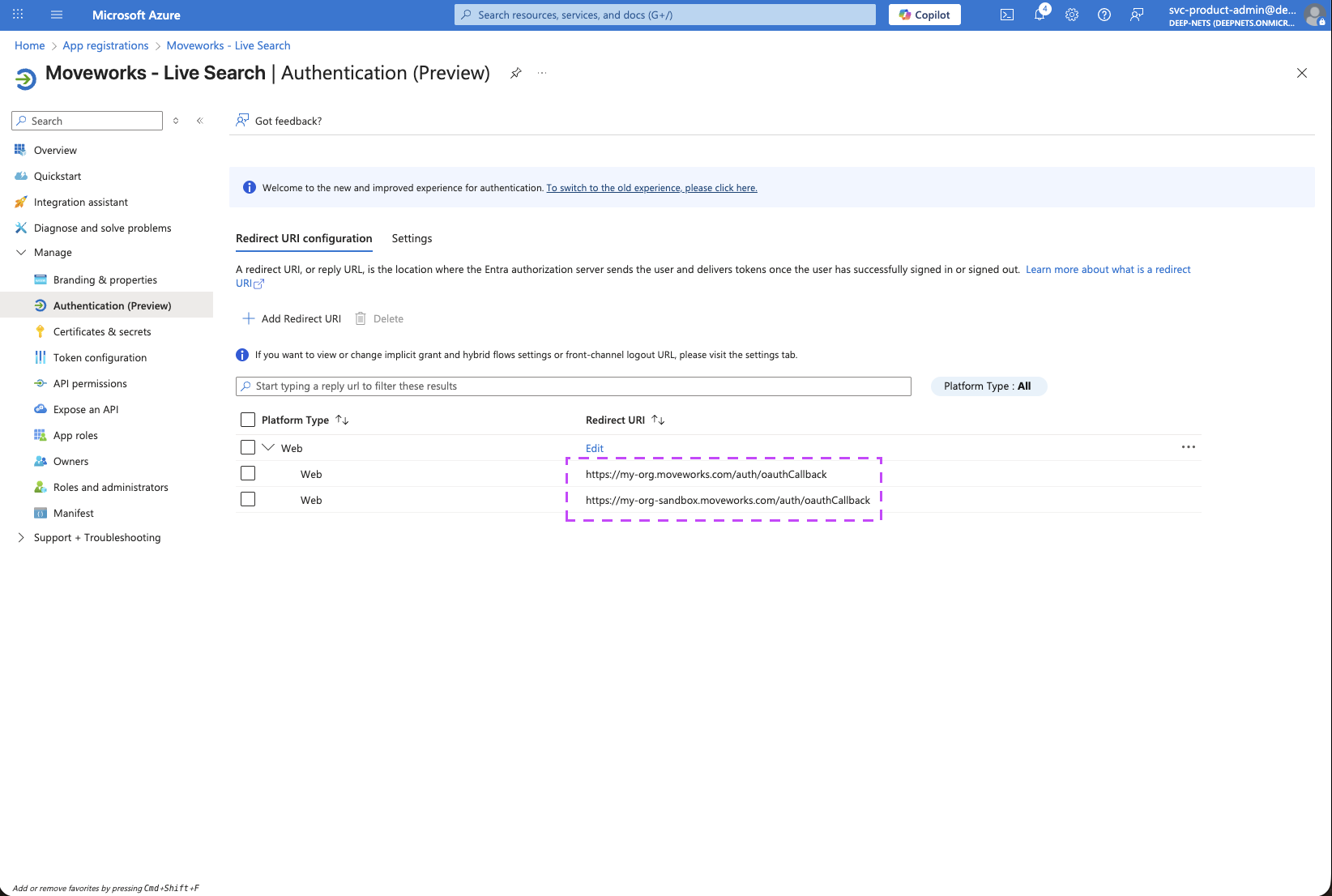
-
You should now notice both of your MyMoveworks URI configured on this page.
2. Setup API Permissions
-
Go to API Permissions to add the required MS Graph Permissions:
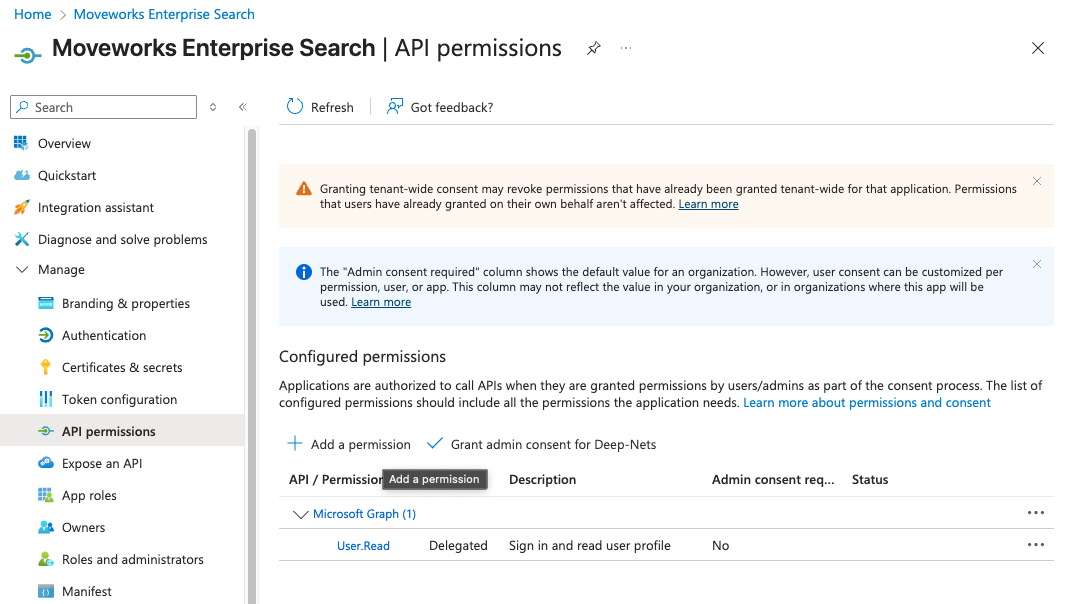
-
Click on Add a permission button. This will open a panel on the right side
-
Select Microsoft Graph.
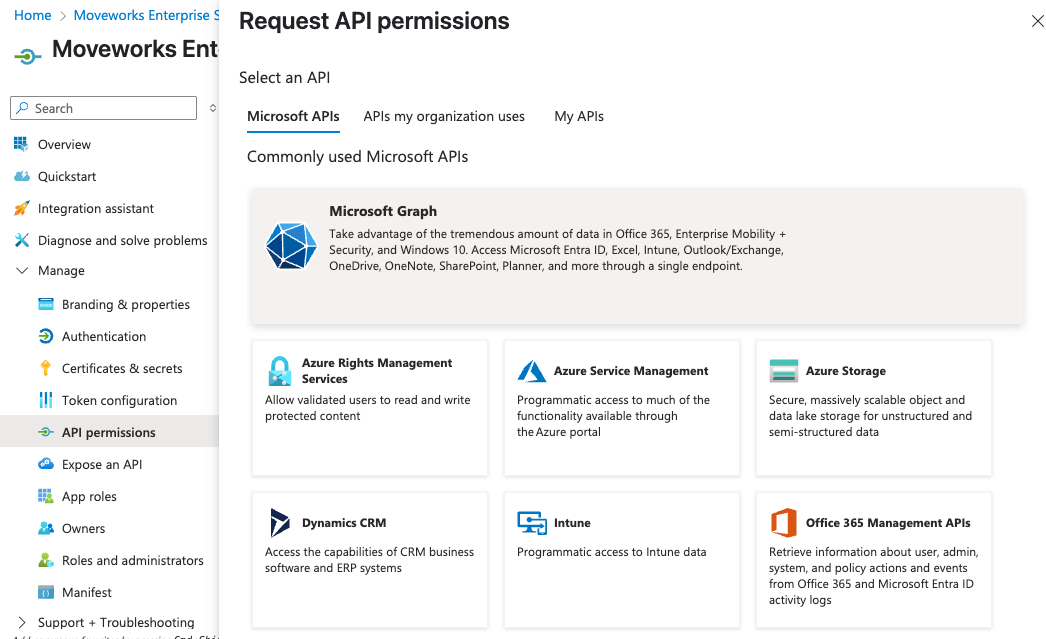
-
Choose Delegated Permissions.
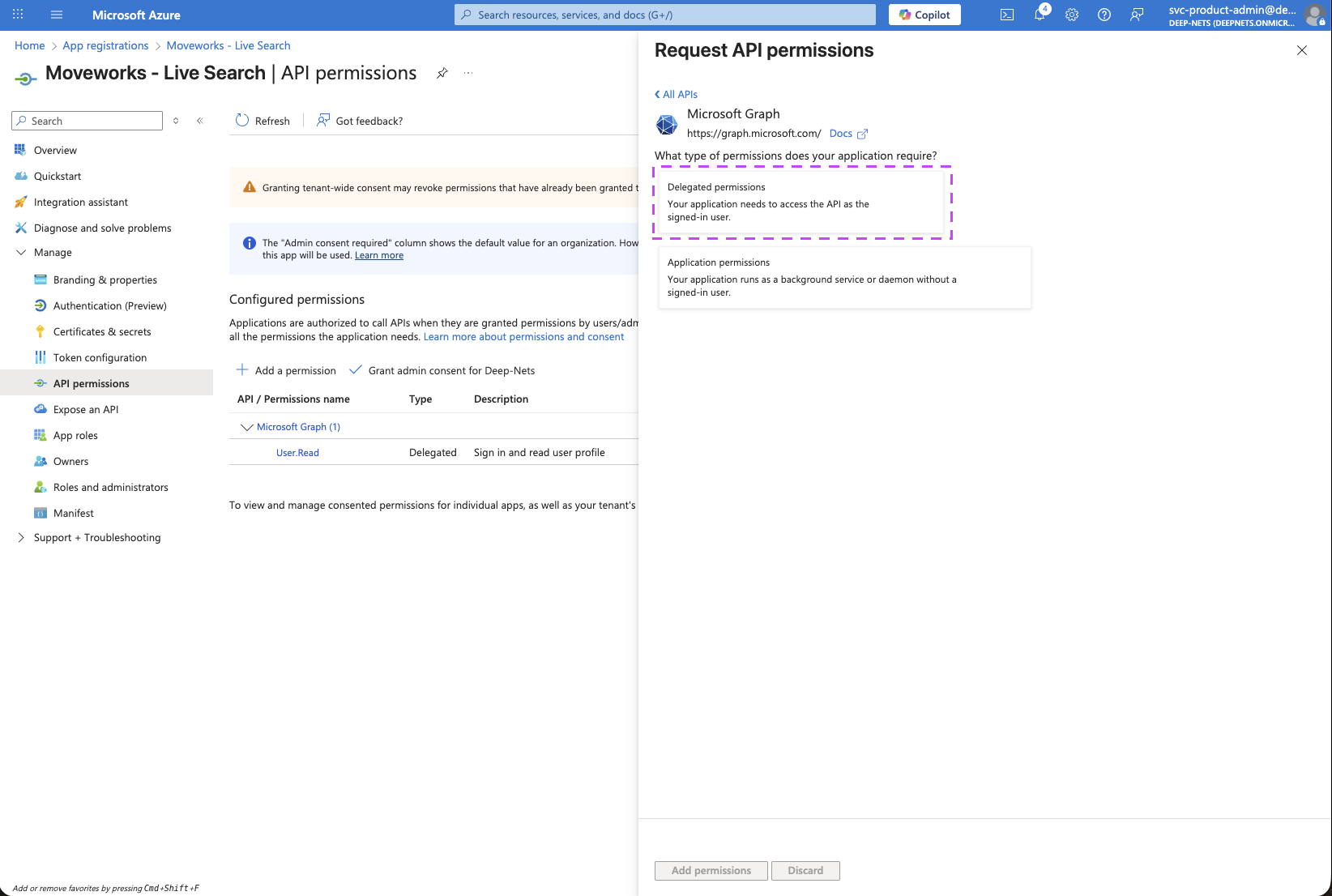
-
Ensure the following Delegated Permissions are added to the application.
Files.Read.All: lets Moveworks read files the user already has access to in OneDrive and SharePoint document libraries, so it can surface relevant results.Sites.Read.All: lets Moveworks read site pages and list items the user can access in SharePoint Online.User.Read: identifies the signed-in user.offline_access: allows Moveworks to store a refresh token so the user doesn’t have to re-consent every time they search.
-
Click on Add permissions after selecting all of the above permission scopes.
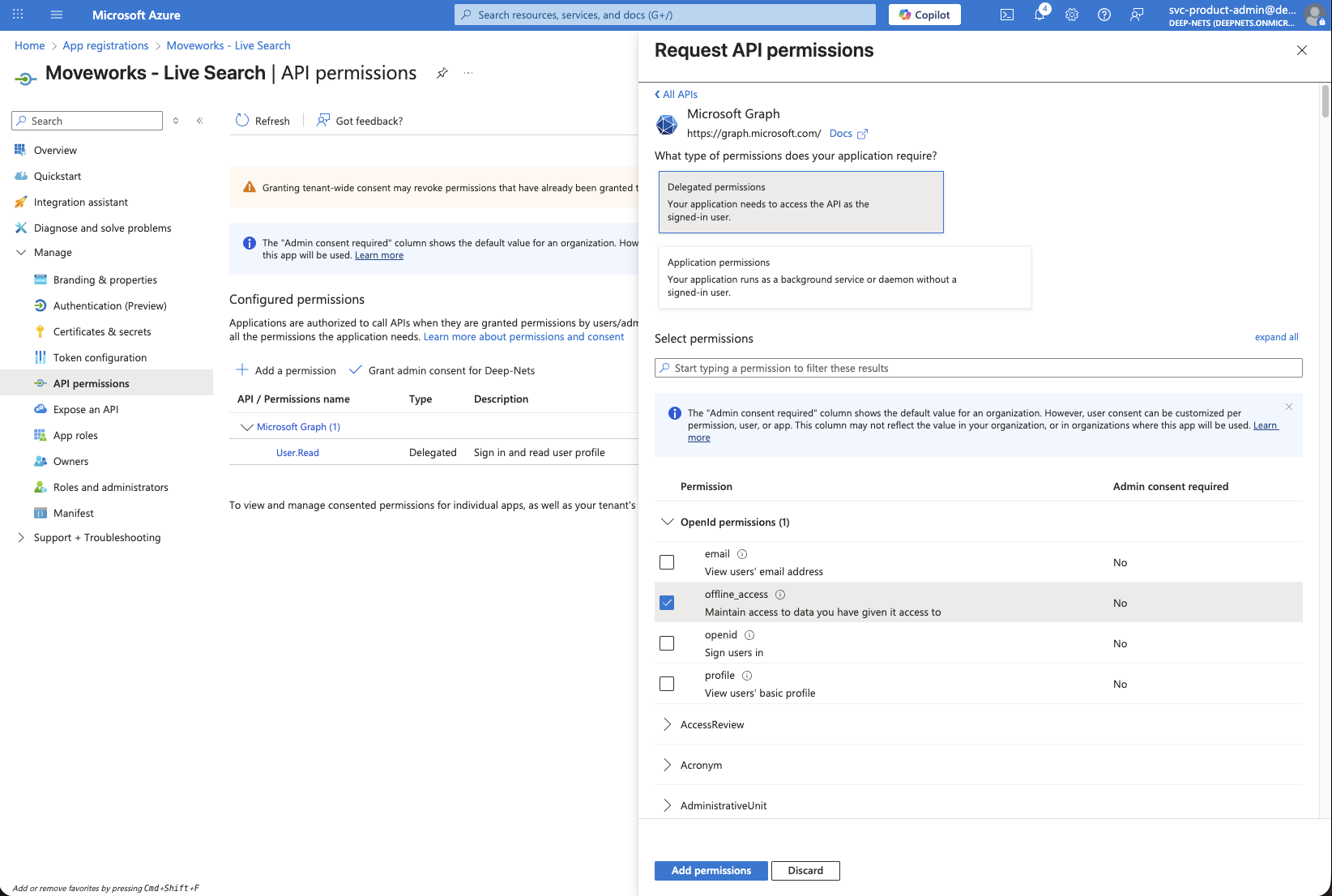
-
Verify that all 4 permission scopes are present under Configured permissions.
-
Click on the Grant admin consent for your-org button to make sure all permissions are available for all users to grant access.
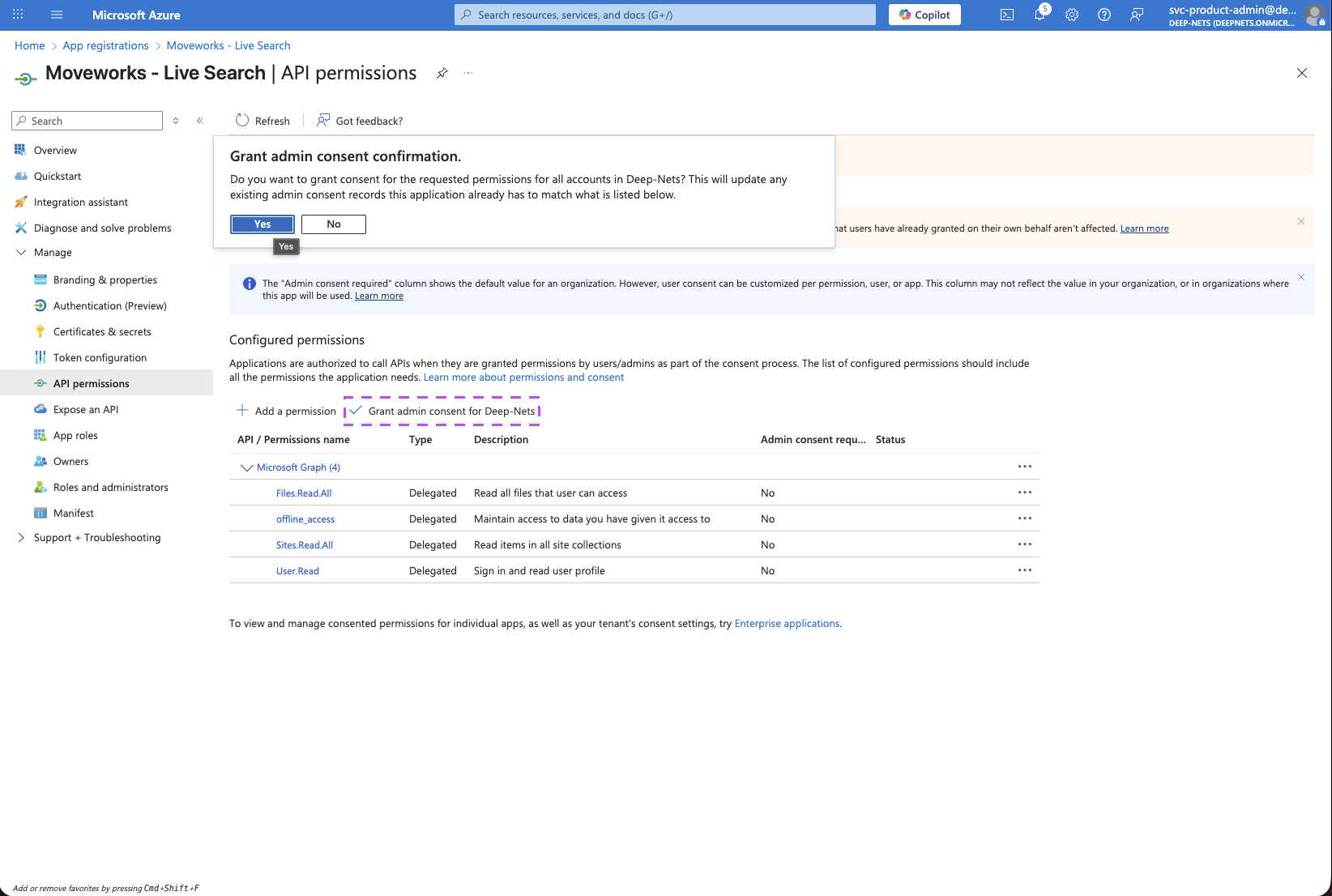
-
If this panel appears, click Yes, add other granted permissions to configured permissions then Save and continue, then Grant admin consent, and then Yes.


-
You will see green checkmarks on the newly added permissions if this was successful.
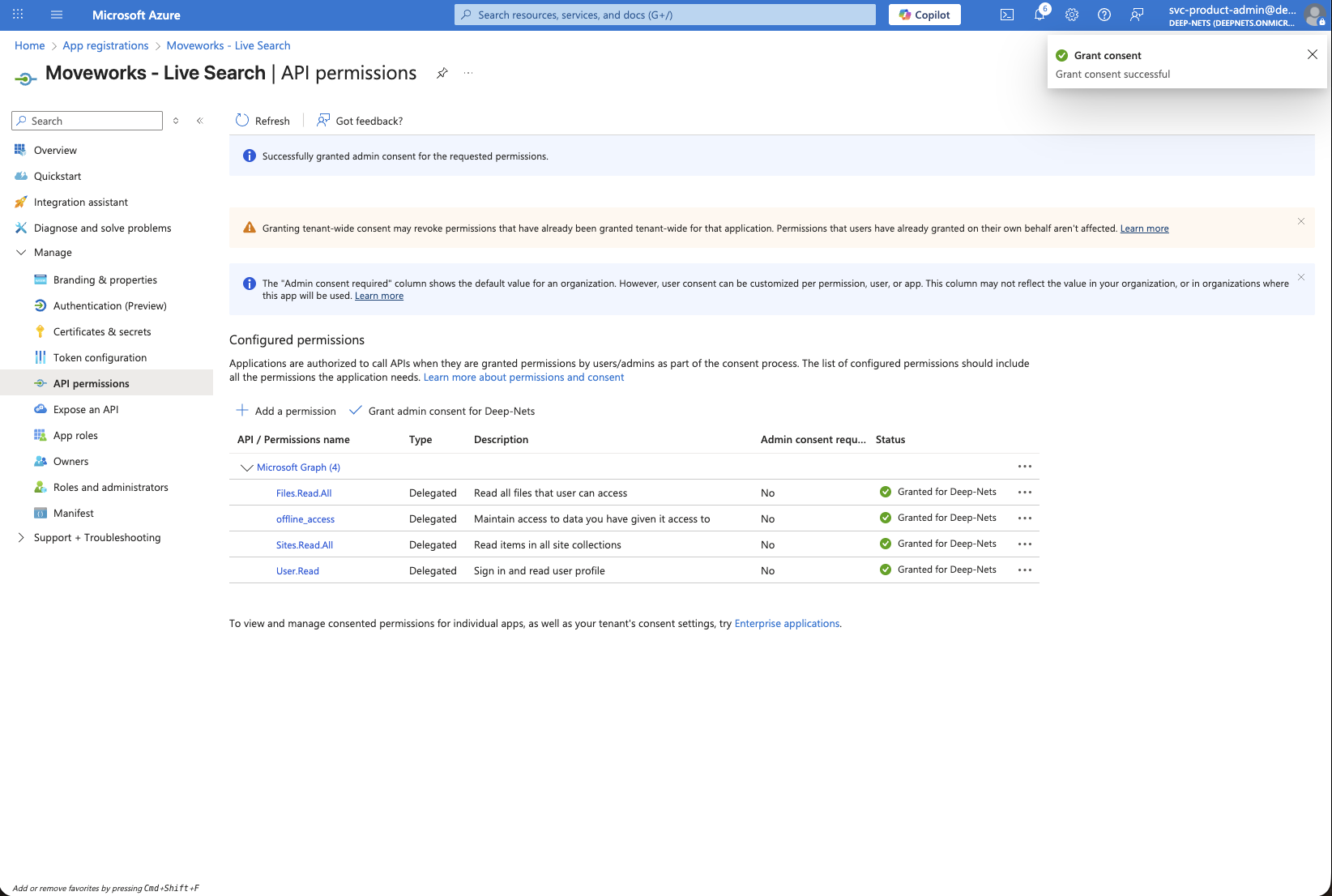
3. Generate Client Secret
Next, we will need to create a Client Secret for the Registration to connect it to Moveworks.
-
Navigate to the App you created above -> Certifications & secrets
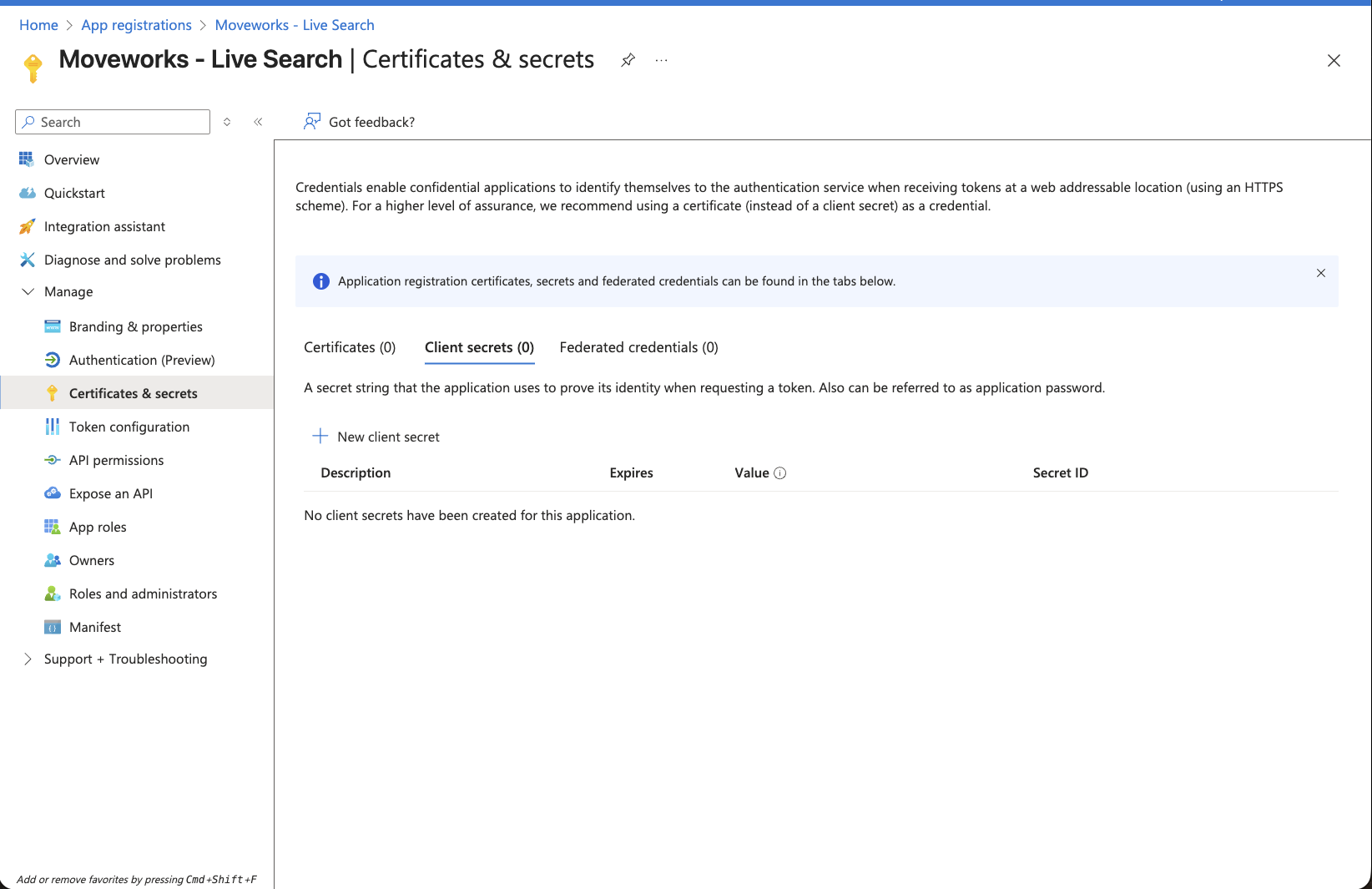
-
Click on New client secret button. This will open a panel on the right side.
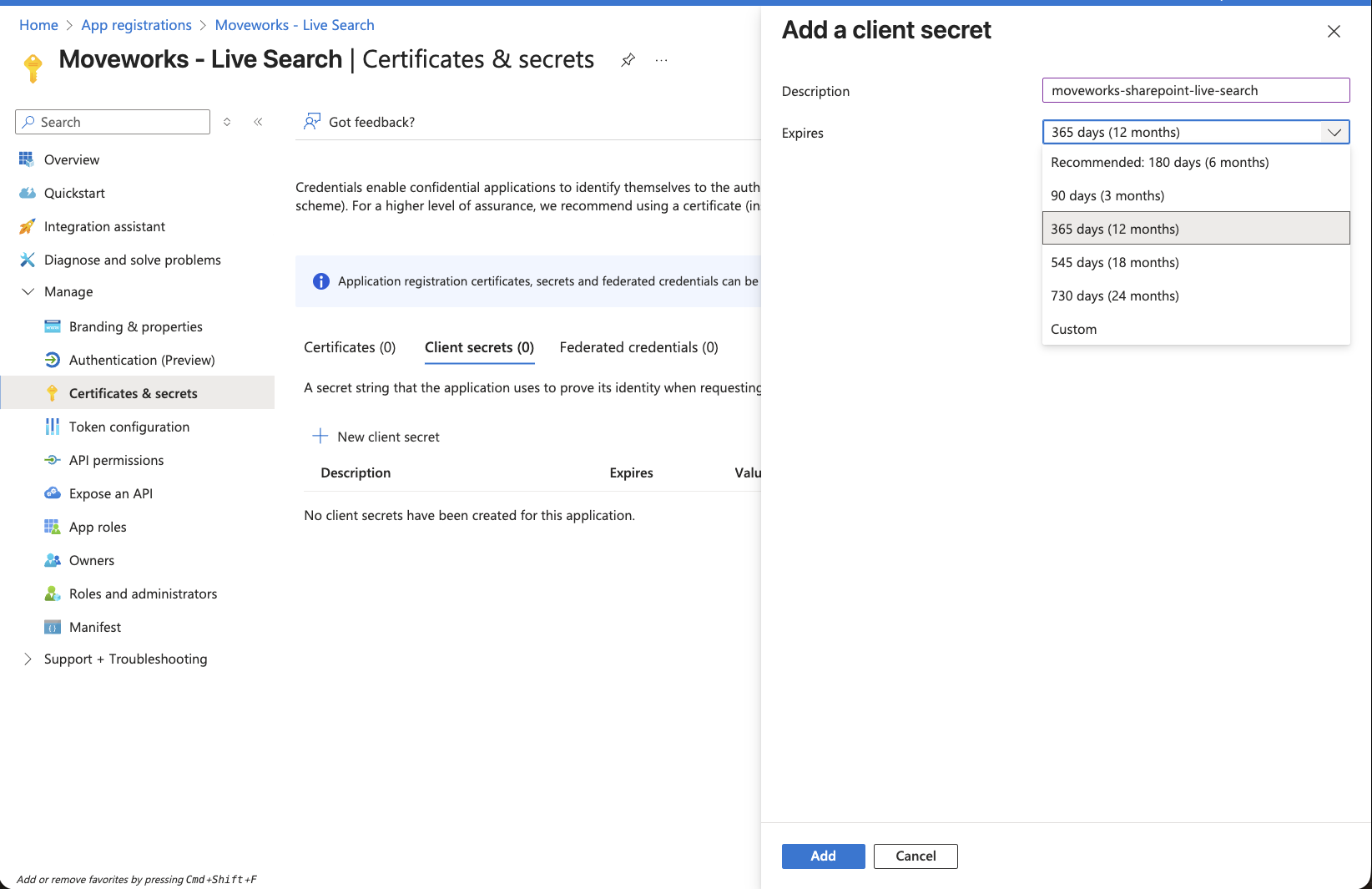
-
Set the description and expiry of this credential based on your org's policy and click on Add.
-
This will create a new entry on the Client secrets table
-
Make sure to copy the secret present in the Value column and store it in a secure location.
Note: Once you create the Secret, make sure to save it right now as it cannot be recovered later.
-
Go back to the Overview page, to capture the following details:
Directory (tenant) IDApplication (client) ID
You have now completed all required steps to create a new Enterprise Application and generate the requisite credentials to setup a connector within Moveworks Setup for enabling Live Search. You should have the following details with you now:
Application (client) IDDirectory (tenant) IDClient Secret
Setup in Moveworks
Connector Creation
- Log in to your org's MyMoveworks portal
- Navigate to Moveworks Setup > Connectors > Built-in Connectors
- Click Create New
- Search and Select Sharepoint OneDrive NG (Next Gen)
- Click on Next: Add Creds
- Input the following details
- Connector Name : Name this connector for your future reference. Once set, this name cannot be changed.
- Tenant (directory) ID: Enter your Microsoft Entra (Azure AD) tenant ID that uniquely identifies your organization.
- Tenant Domains: Enter all the SharePoint tenant domains to ingest data from across the organization, if you have multiple geo-locations configured. Eg: Enter org1 for domain_url org1.sharepoint.com and org2 for domain_url org2.sharepoint.com
- Region (optional): Select an option that will be used to establish the base URL. If no selection is made, the default option will be commercial. If GOV L4 is selected .us token url will be created
- Application (client) ID: Enter the Application (client) ID from your Indexing Microsoft Entra app registration's Overview page, used for certificate-based authentication.
- X.509 Certificate SHA-1/SHA-256 Thumbprint (x5t): Enter the SHA-256 thumbprint of your uploaded certificate from Microsoft Entra, used to verify certificate authenticity (format: hexadecimal string without colons or spaces).
- Private Key: Upload the private key as a PEM file that corresponds to the certificate uploaded to your Microsoft Entra app registration.
- Application (client) ID: Enter the Application (client) ID from your Live Search Microsoft Entra app registration for delegated/user-consent authentication.
- Application Client Secret: Enter the client secret value from your Live Search Microsoft Entra app registration for delegated/user-consent authentication.
- Click Save. This connector will now be used to configure content ingestion from Sharepoint Online and enable live search from OneDrive. Refer to the steps mentioned below.
Configuring SharePoint Online and OneDrive for Enterprise Search
Initialising setup
-
Log in to your org's MyMoveworks portal
-
Navigate to Moveworks Setup > Answers > Ingestion > Enterprise Search
-
Click on Create New or Get Started
-
Select SharePoint Online & OneDrive from the dropdown list and click on Get Started
-
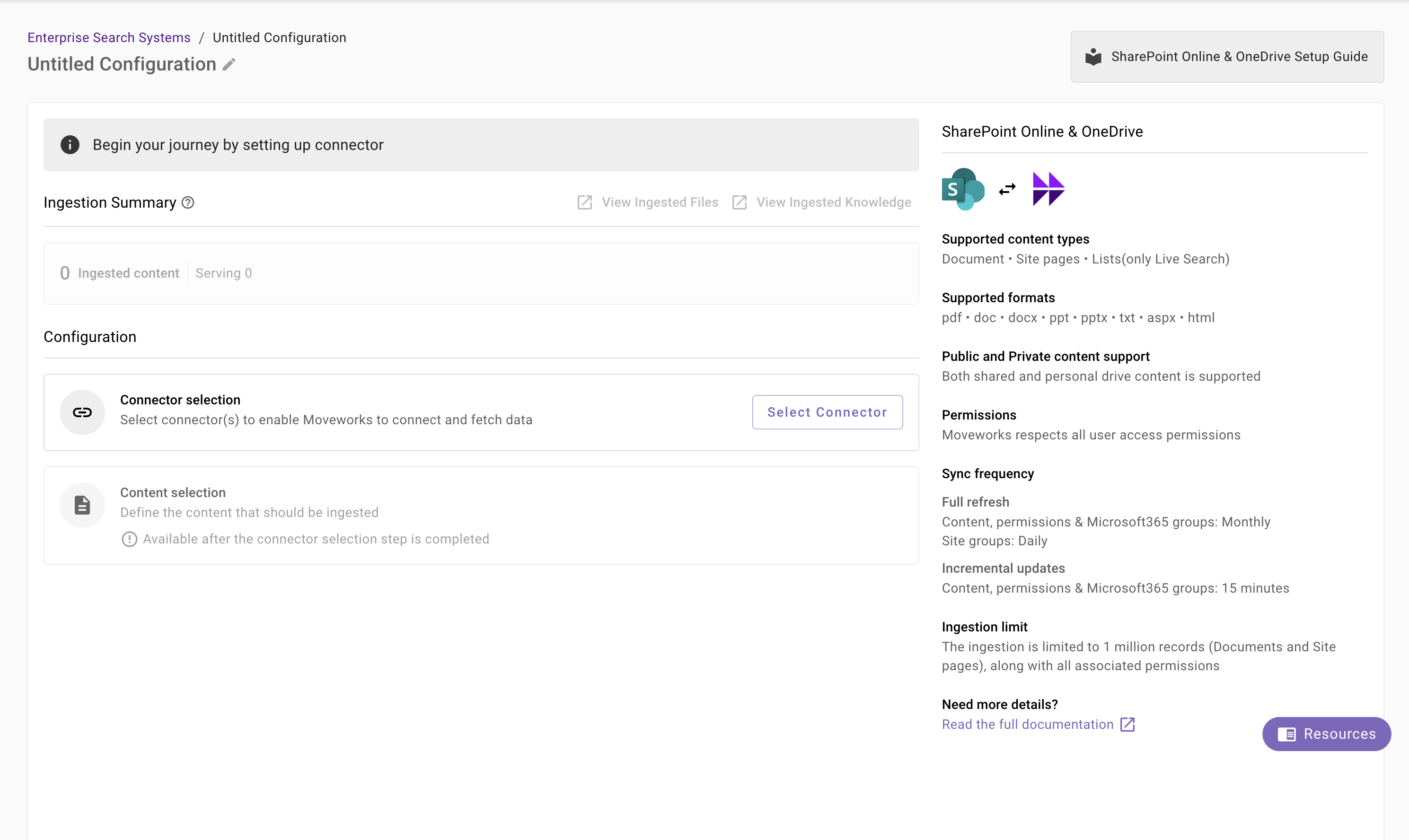
You will be redirected to the SharePoint Online & OneDrive ingestion overview page. In the overview page, you will find few info blocks and few configuration blocks.
- System Overview: This presents an overview of SharePoint Online & OneDrive support from Moveworks
- Ingestion Summary: This provides information on the count of records that has been ingested and serving. The values will appear after the first successful ingestion run.
- Connector Selection: In this configuration block, you are required to select the required connector to enable Moveworks to connect and fetch data or enable live search.
- Content Selection: In this configuration block, you are required to define the content that should be ingested within Moveworks
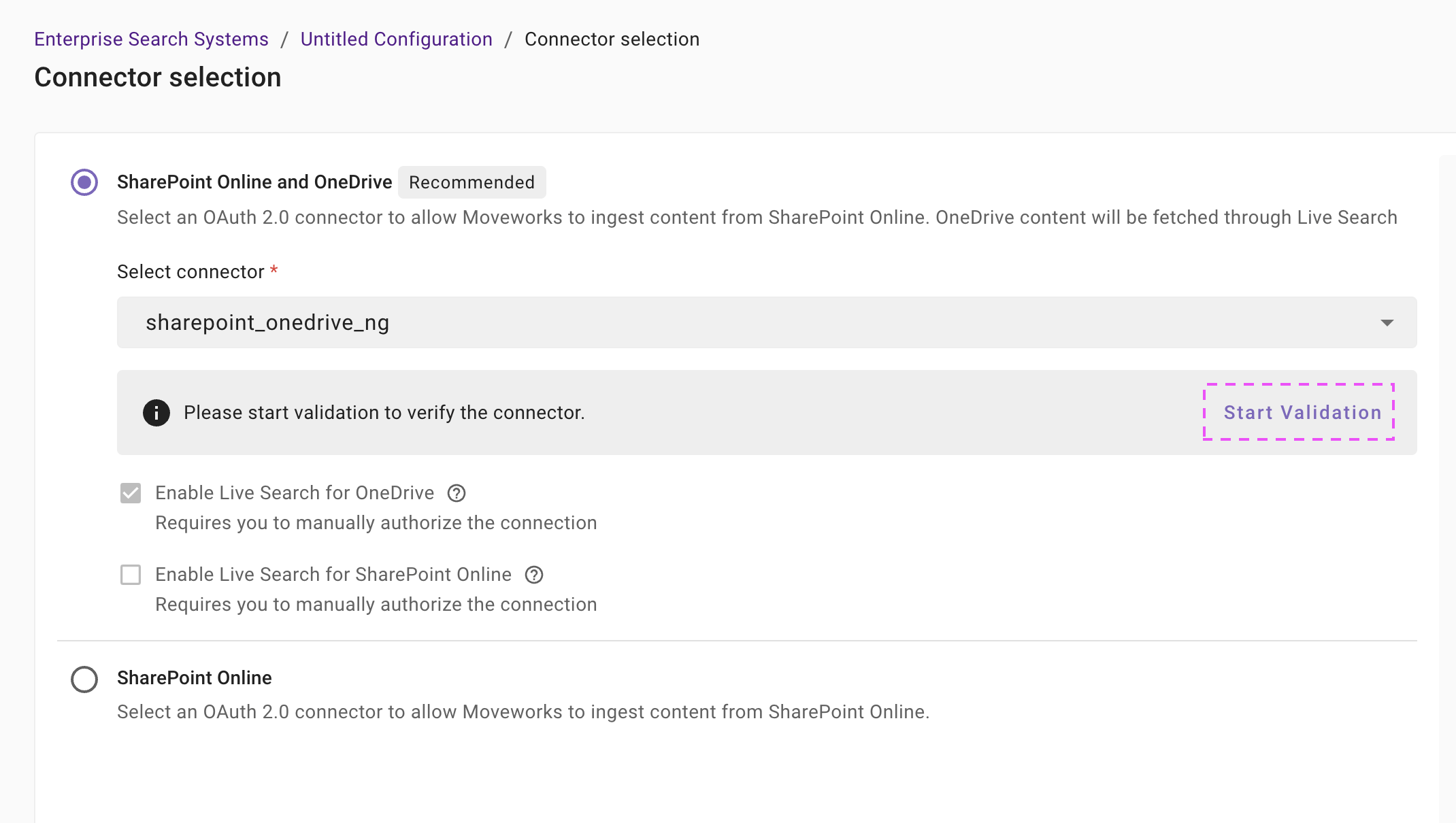
Connector selection and validation
-
Once you click on Select Connector, a connector setup screen will appear as follows
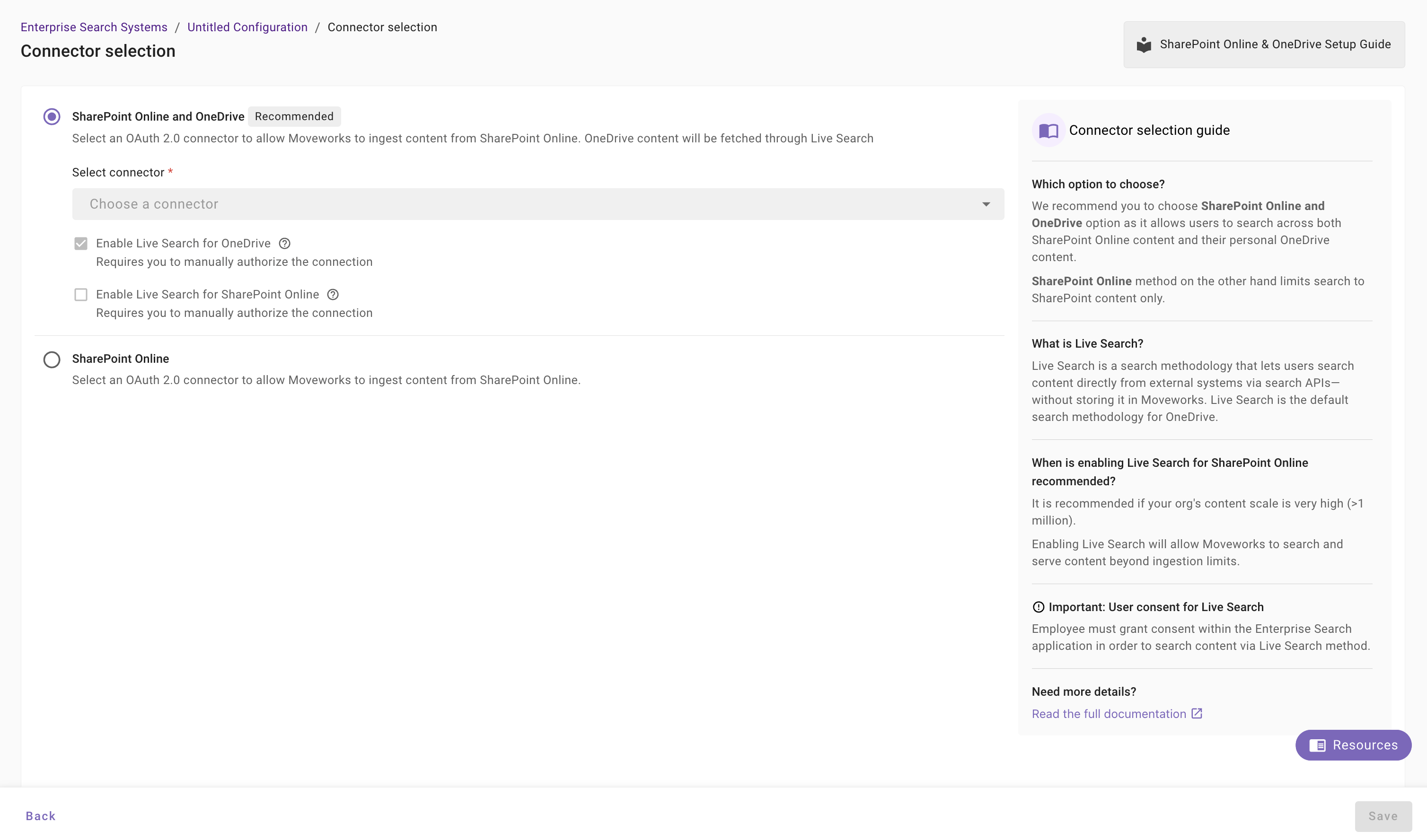
Note: You have a choice here to either select - SharePoint and Online and OneDrive or just configure SharePoint Online. In each of these respective cases, you will also have the option to select SharePoint Online content retrieval via live search.
-
For any of these options, select the connector (from the dropdown) that you have created in the Connector Creation step.
Please note: Only the Sharepoint OneDrive NG (Next Gen) connectors will appear in this list.
-
Once the connector is selected, you need to click on Start Validation to validate the connector credentials and required scope.
Connector Validation
This is a mandatory step in order to save the configuration and move to the next step.
Moveworks validates the selected connector to check:
- Auth: Moveworks validates if the connector has right credentials to authenticate
- Content: Moveworks validates if connector has right scopes to fetch content
- Permissions: Moveworks validates if connector has right scopes to fetch user permissions
- Users: Moveworks validates if connector has right scopes to fetch user data
- Groups: Moveworks validates if connector has right scopes to fetch Microsoft365 groups data
- Site Groups: Moveworks validates if connector has right scopes to fetch site groups data from the specified Site.
-
In case of SharePoint Online, an example Site URL is required to conduct Connector Validation for all resources. On the dialog box that appears, please configure one of your Site's URL to start the validation process. The Site URL must be of the format:
https://{org}.sharepoint.com/{site_url_type}/{site_name}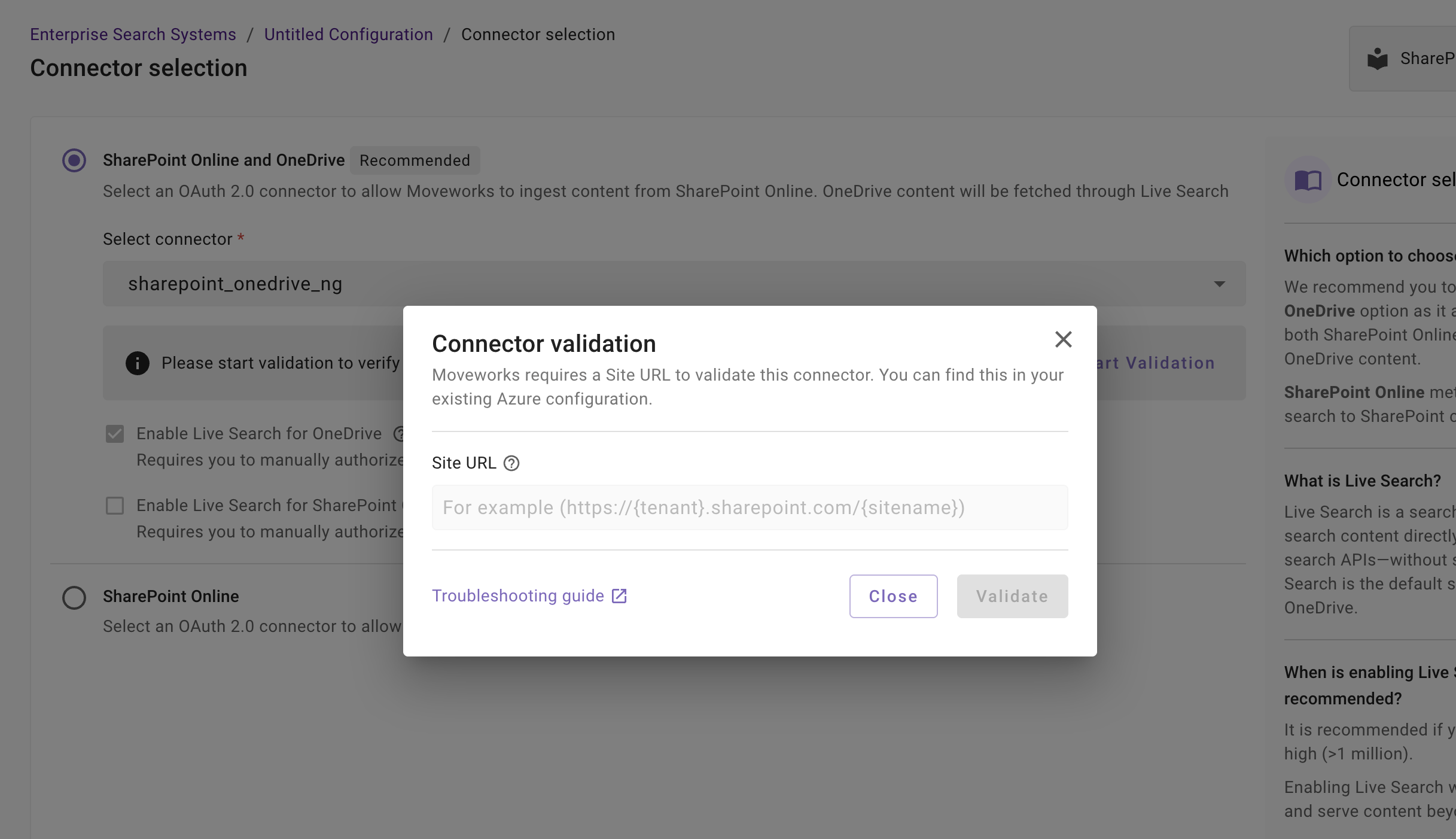
-
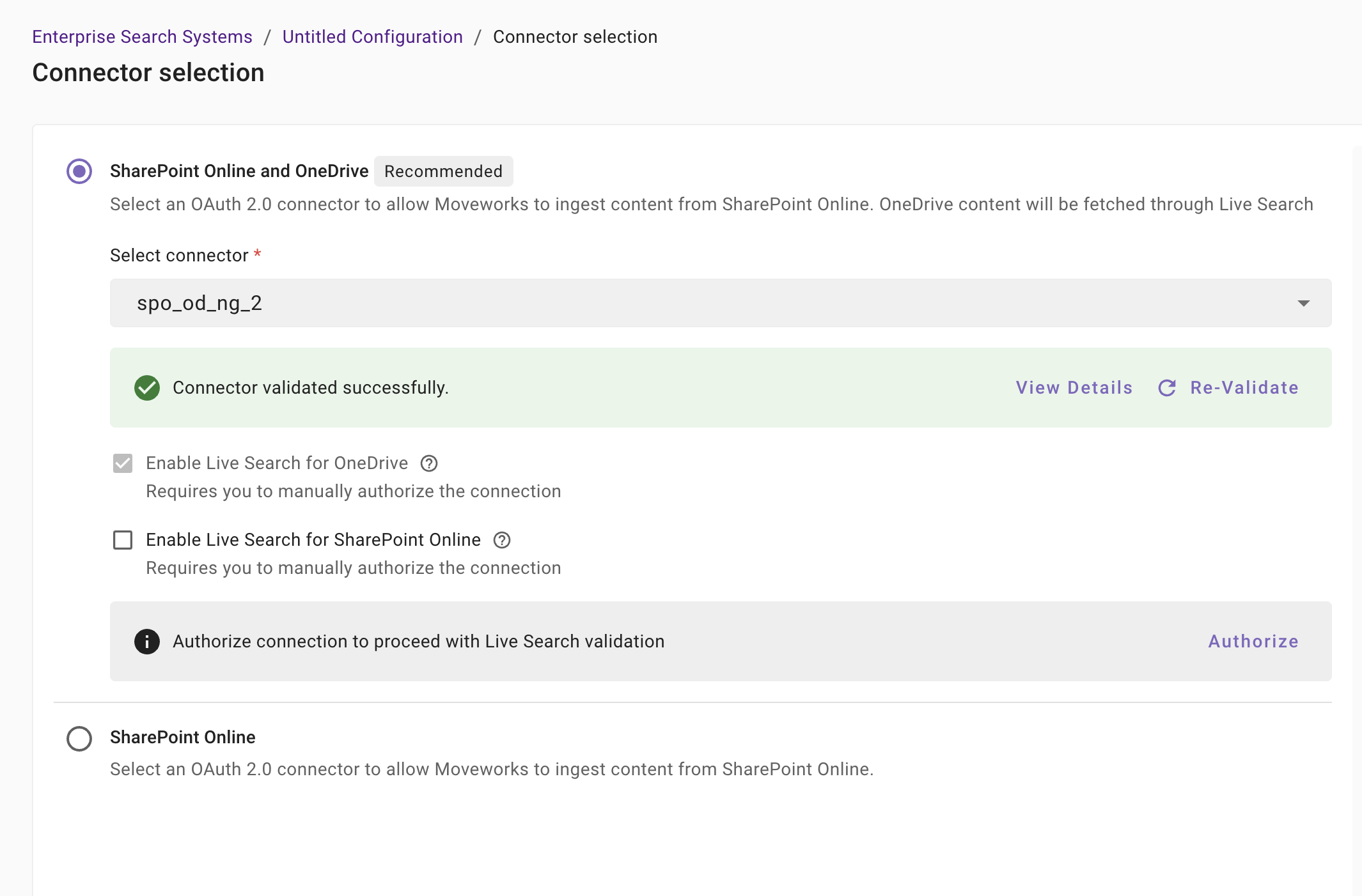
If the connector is validated successfully, you will see a green info banner as follows. This will also enable selecting the Live Search options and the Connector Validation for Live Search as well.
- If there are any credentials or scope issues, you will receive an error message as follows. Click on View Details to identify the issue. Refer to this step-by-troubleshoot guide (link to be added) to rectify any validation errors.
-
In case of the 1st option, SharePoint Online and OneDrive, we currently only support Live Search for searching content from user's OneDrives. Therefore, the Live Search button is enabled by default. If you would like to not opt for Live Search at all, you can select the 2nd option, select the connector and complete the setup connector selection step here.
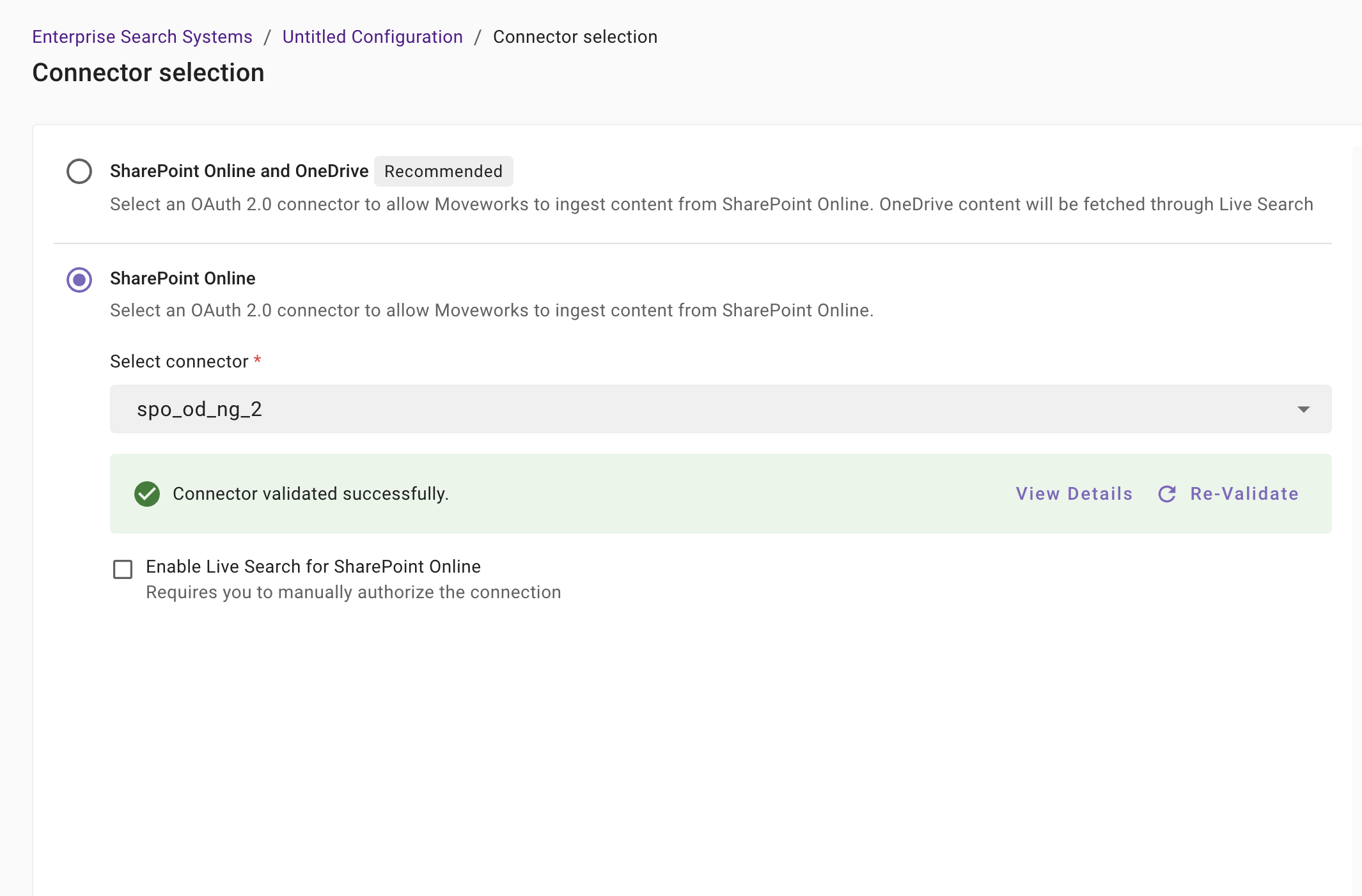
-
If you want to enable Live Search from any of the sources, you will first have to click on Authorize to allow Moveworks to generate the credentials required to validate the live search connection.
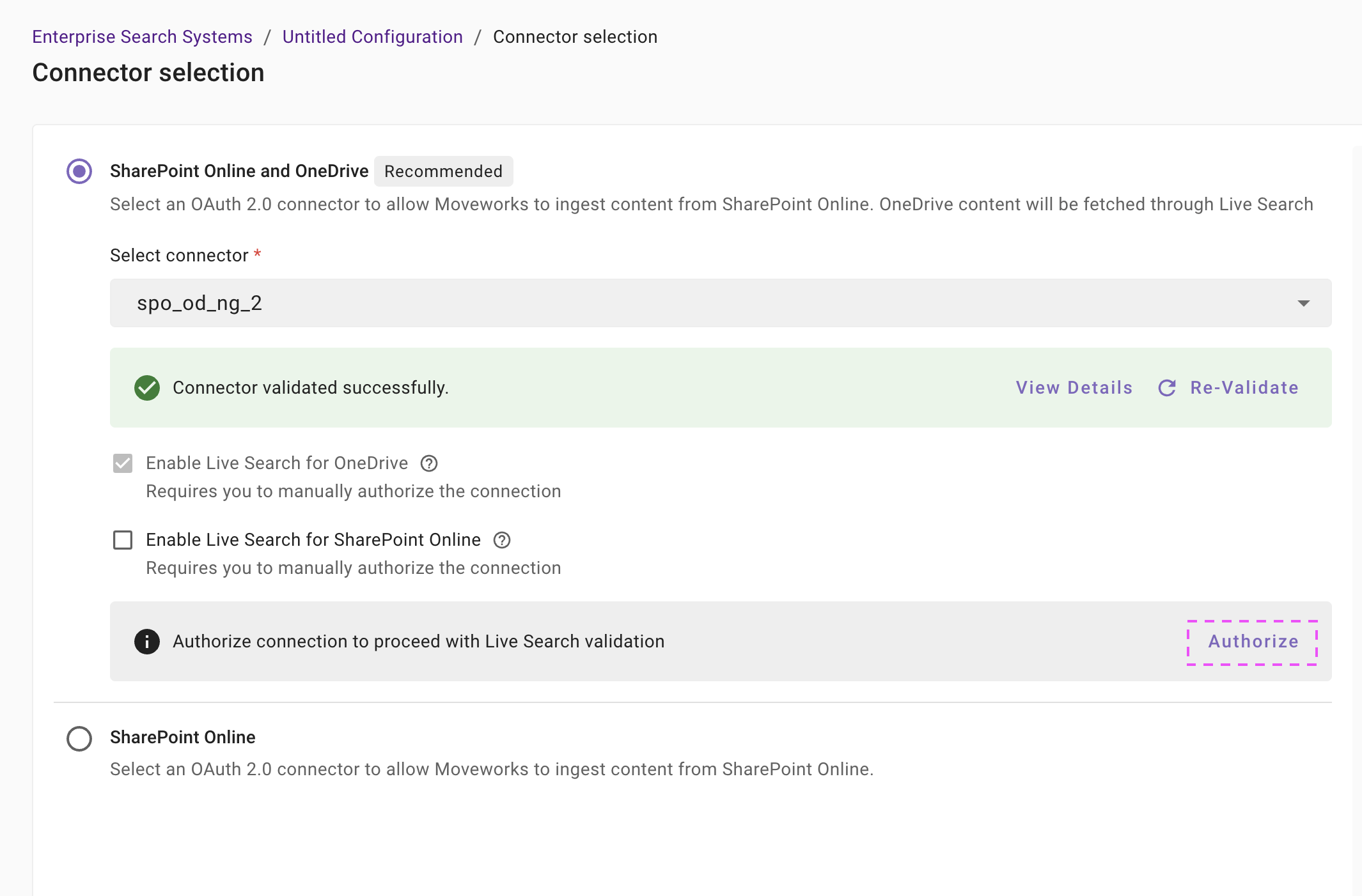
-
Once you have signed-in to your Microsoft User and approved the App, the authorization step will be completed and you will be redirected back to the Moveworks Setup page to click on Start Validation to continue the validation for live search connection.
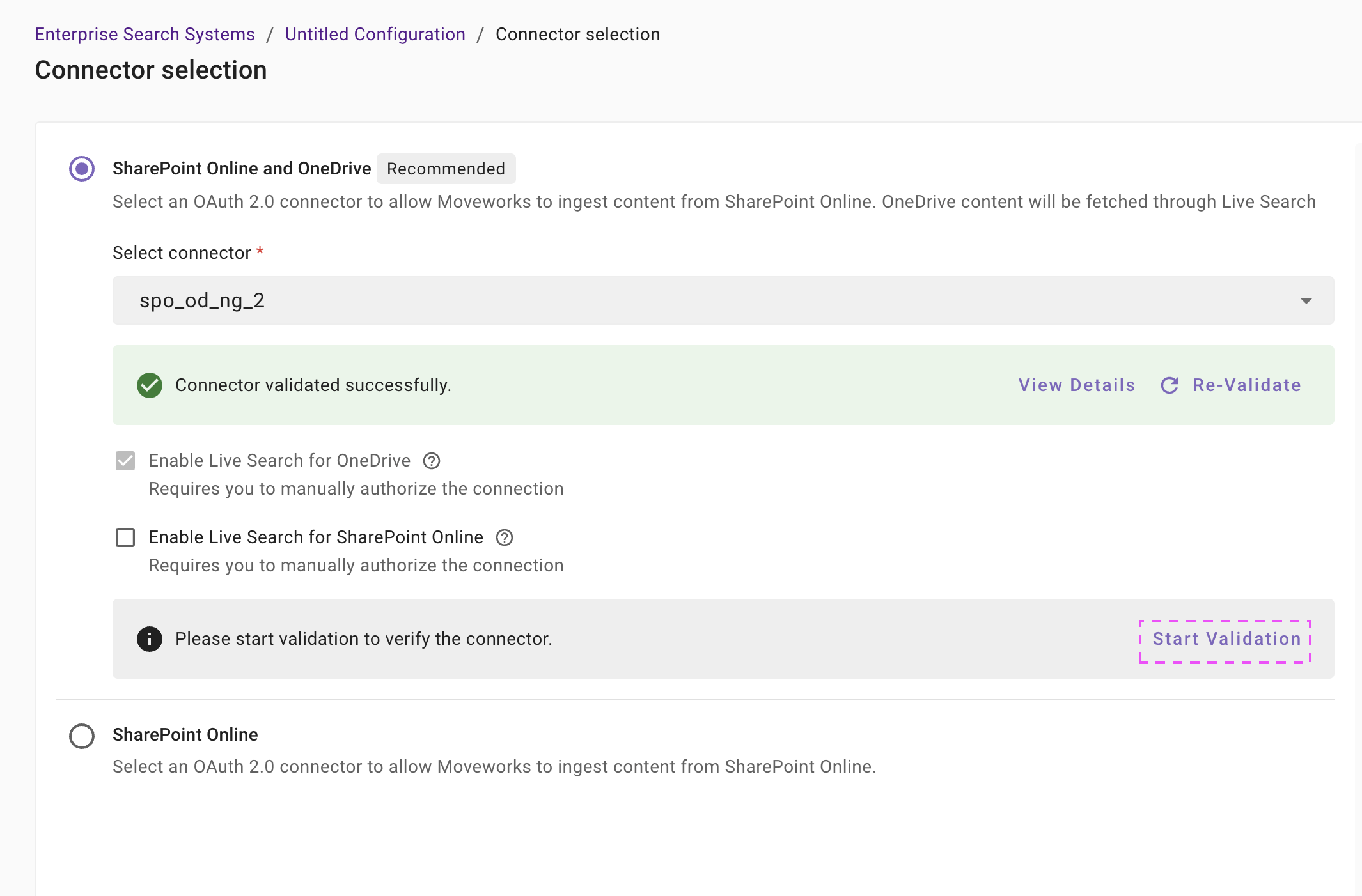
-
If the validation is successful, you will notice another green banner.
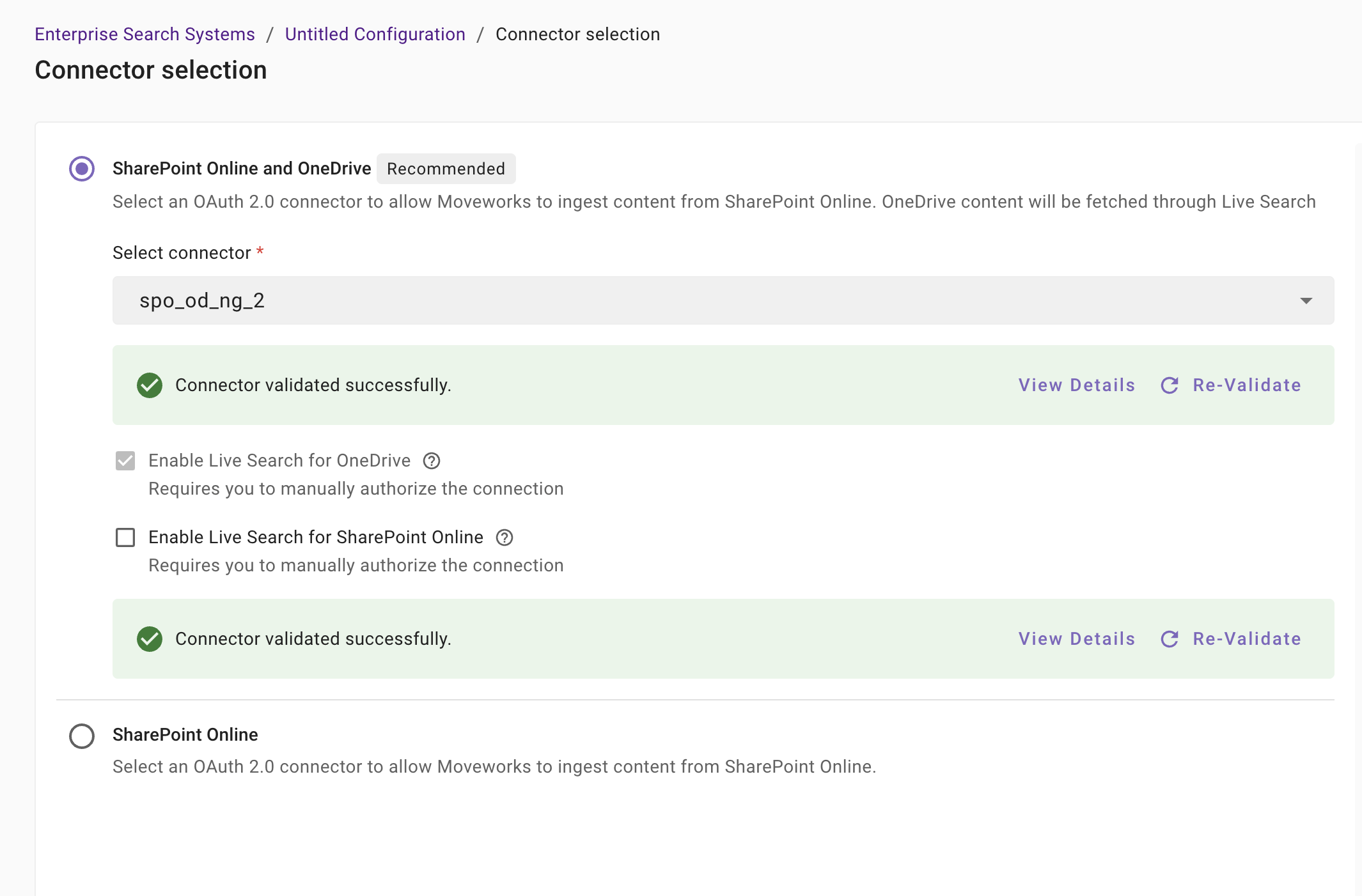
-
Once the connector is completely validated successfully, you will be able to Save the configuration.
-
Input the unique configuration name and Save.
At this stage, only the configuration entry is created. Ingestion doesn't start immediately after this step. You need to configure the Content Selection step to complete the journey. Refer to the next section for details.
-
Once the configuration is saved, you can view the unique configuration name at the top of the screen. You can also click the pencil 🖊️ icon to edit the configuration name.

-
Additionally, you will start seeing an entry of your configuration in the Enterprise Search home page. You can click on your configuration to go to edit/ complete the configuration.
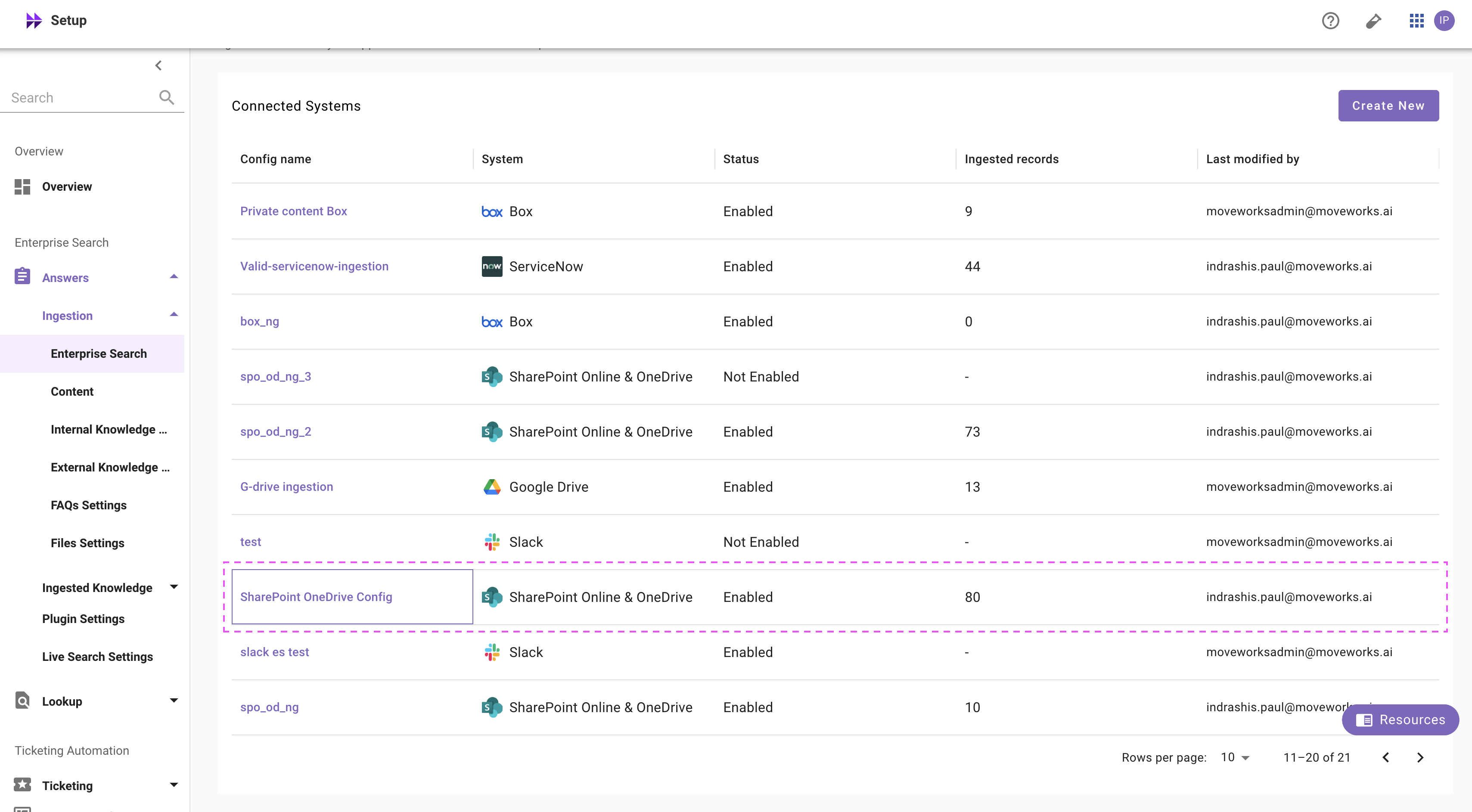
Content Selection
Once the connector selection step is complete and the configuration is saved, you will now be required to define the scope of content that will be ingested in Moveworks.
-
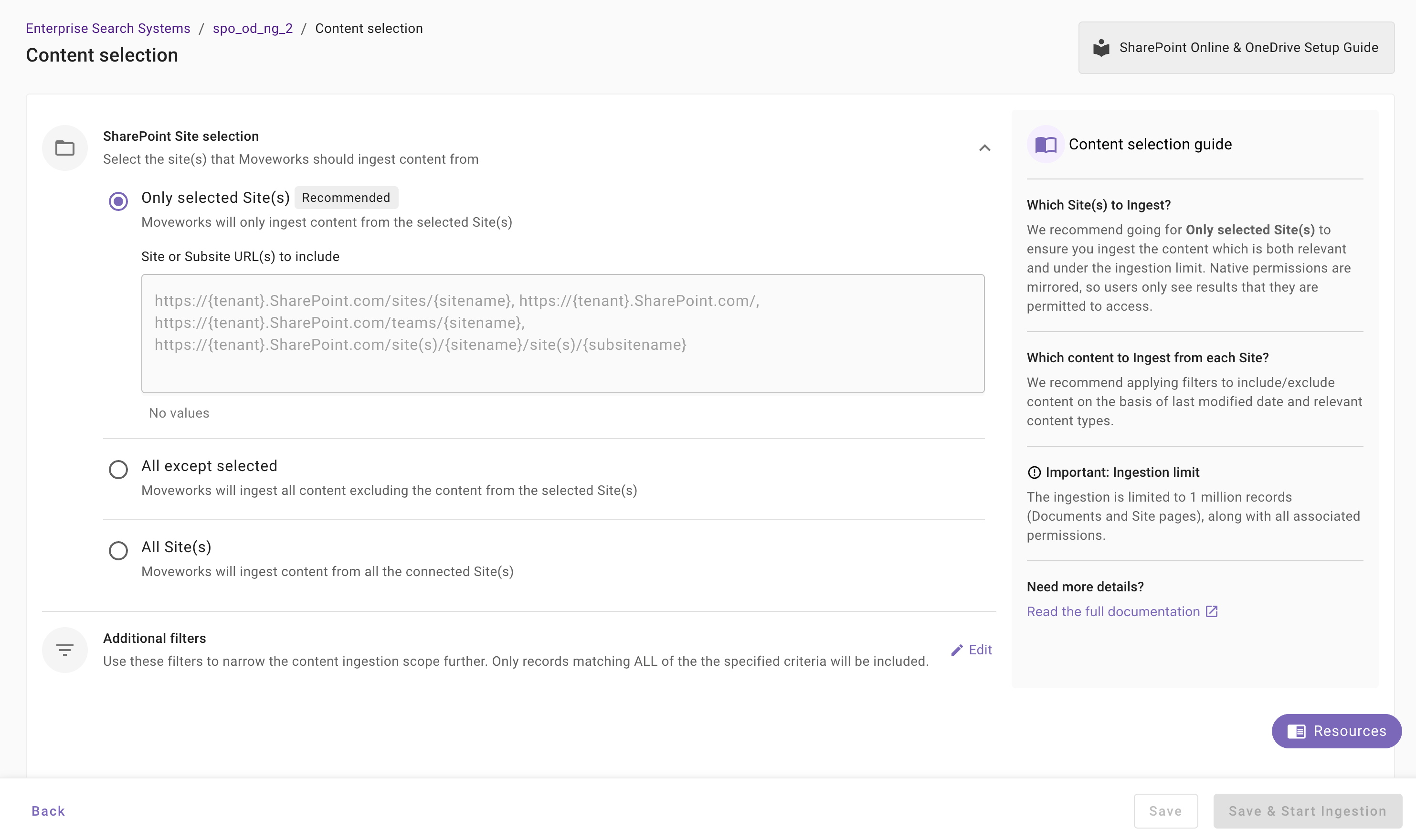
Once you click on Select Content, a content selection screen will appear as follows.
-
In this screen, you are required to define the Site URLs from which Moveworks will ingest content and apply filters (optionally) to filter down the content further.
-
Sharepoint Site Selection: This is a mandatory configuration. This configuration defines which Sites Moveworks will crawl and ingest content from. As an admin, you get three options
-
Only selected Sites(s) (Recommended): Moveworks will only ingest content from specified Site URLs.
When to choose this option? Choose this option if you want content to be served only from a subset of Site URLs. For example - Let's assume, the Azure App has access to 15 Sites or All Sites, but you want content to be served only from 5 Sites, then you choose this method.
How to configure? Enter comma separated Site URL(s).
-
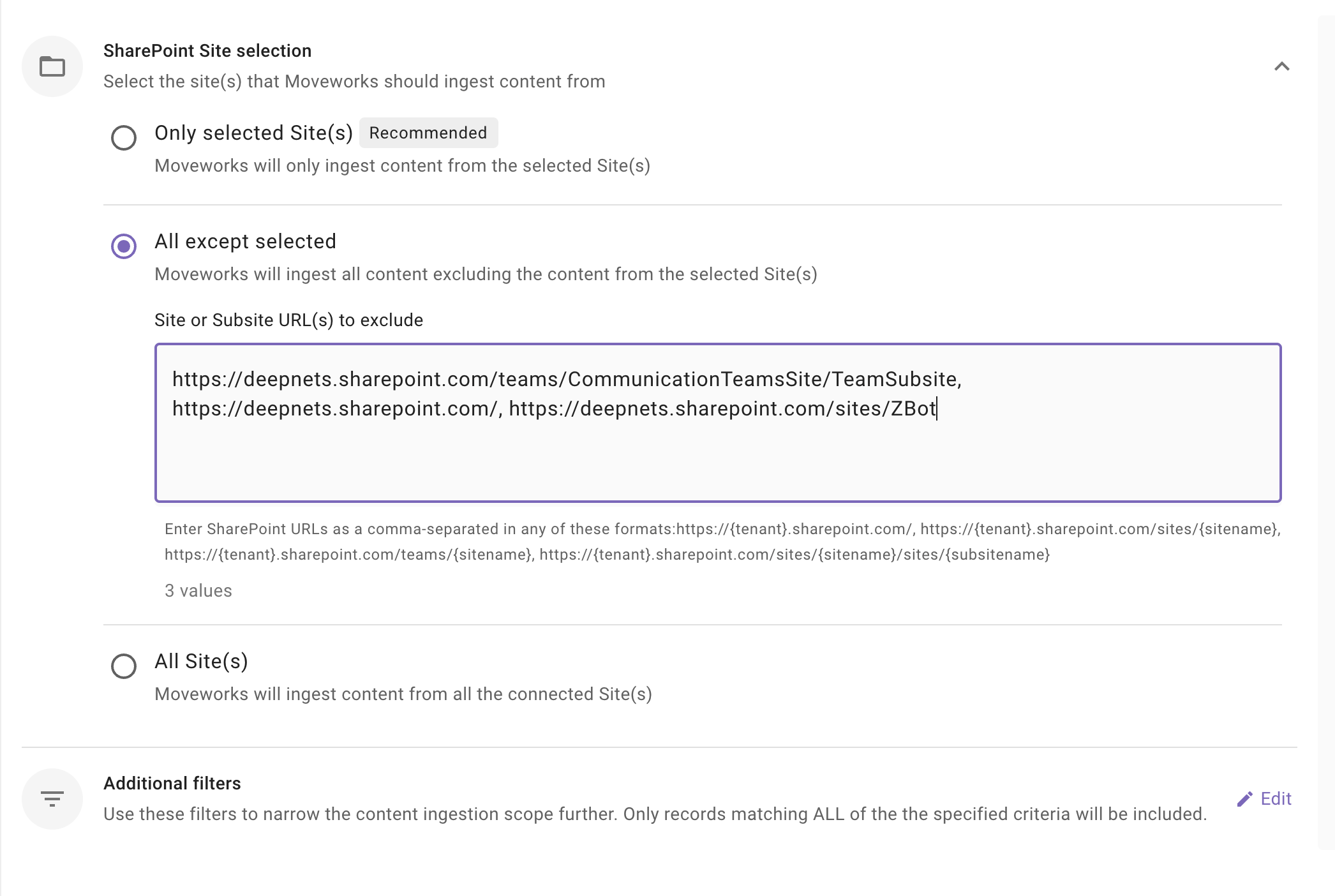
All except selected: Moveworks will ingest content all except specified Sites.
When to choose this option?
Choose this option if you want content to be served from all except few Sites. For example - Let's assume, the Azure App has access to All 100 Sites, but you want content to be served from 96 Sites, then you choose this method and specify the 4 Site URLs from which Moveworks should not ingest.
Important Note: The Azure App must be configured with
Sites.Read.Allpermission scope to enable selecting this option.How to configure? Select this option and enter comma separated Site URL(s).
-
All Sites: Moveworks will ingest content all applicable spaces
When to choose this option?
Choose this option if you want content to be served from All Sites within your SharePoint tenant. For example - Let's assume, your SharePoint tenant contains 100 Sites, and you want content to be served from all 100 Sites, then you choose this method.
Important Note: The Azure App must be configured with
Sites.Read.Allpermission scope to enable selecting this option.How to configure? Select this option. You are not required to specify the Site URLs in this scenario.
-
-
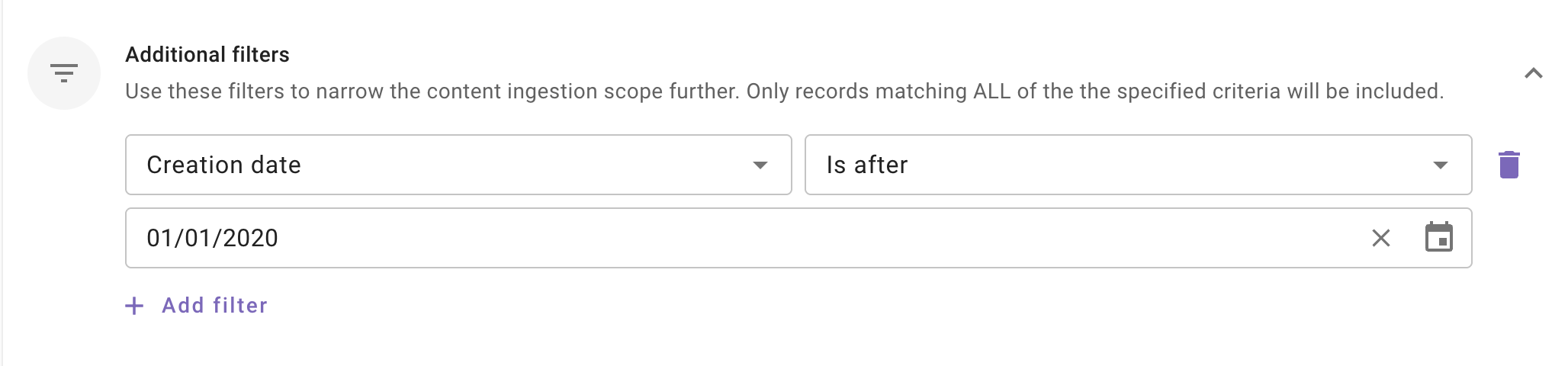
Additional Filters: Use these filters to narrow the content ingestion scope further. Only records matching ALL of the the specified criteria will be included.
This is an optional configuration. Moveworks recommend using these filters only if your dataset is very large (i.e. >1million records) so that only relevant content is ingested and served to your employees.
Currently following filters are supported:
- Modified date: Use this filter to include only those content records whose Modified date is after a specified date.
- Created date: Use this filter to include only those content records whose Created date is after a specified date.
Save and Start Ingestion
Once Space selection is configured, you have two options:
-
Save: Clicking this will just save the configuration and not initiate the first ingestion crawl. Use this option, if you would want to complete your configuration in multiple sessions/ sittings.
-
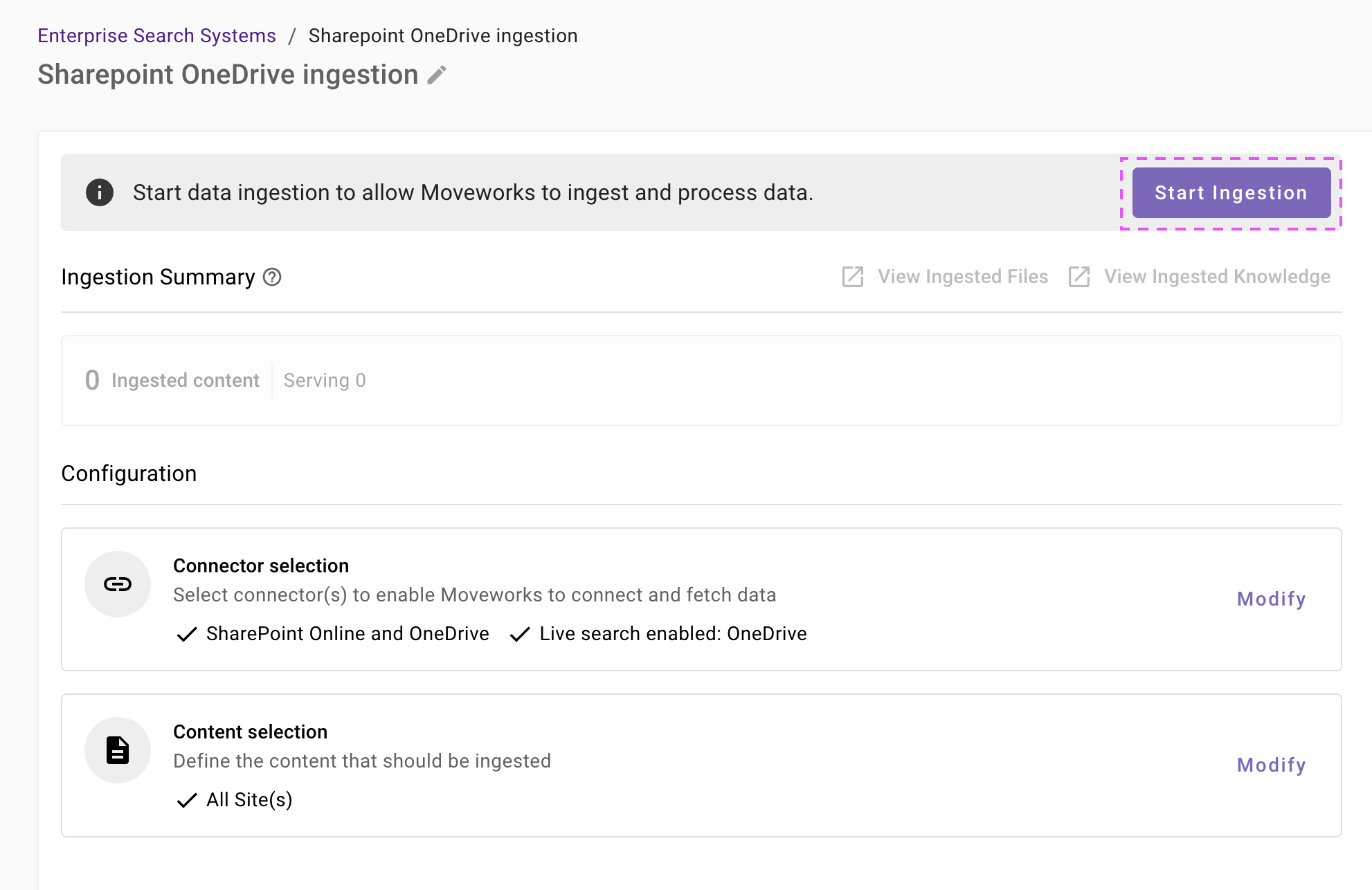
Once you click on Save, you will be redirected to the Confluence overview screen
-
You will notice a banner that prompts you to Start Ingestion
-
Once you are satisfied with your configuration, you can click on Start Ingestion
-
A confirmation popup will come that provides a summary of the configuration
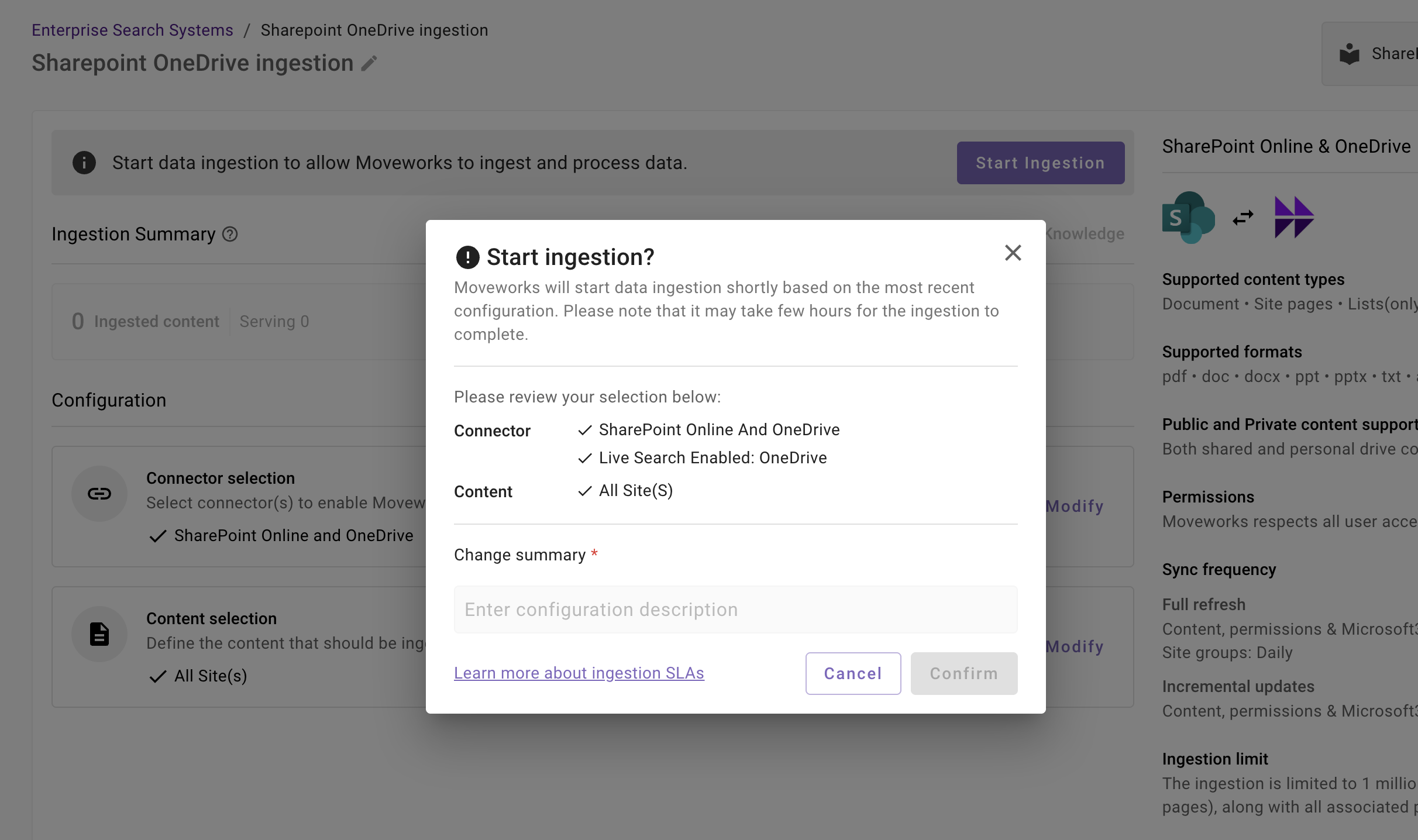
-
Click on Confirm
-
After you click on Confirm, ingestion will start shortly.
-
For the first crawl to complete, this generally takes anywhere from few hours to 48 hours depending upon the size of the data.
-
-
Save and Start Ingestion: Click this option if you have completed and validated your content selection configuration and you are ready to initiate the first ingestion crawl.
-
A confirmation popup will come that provides a summary of the configuration
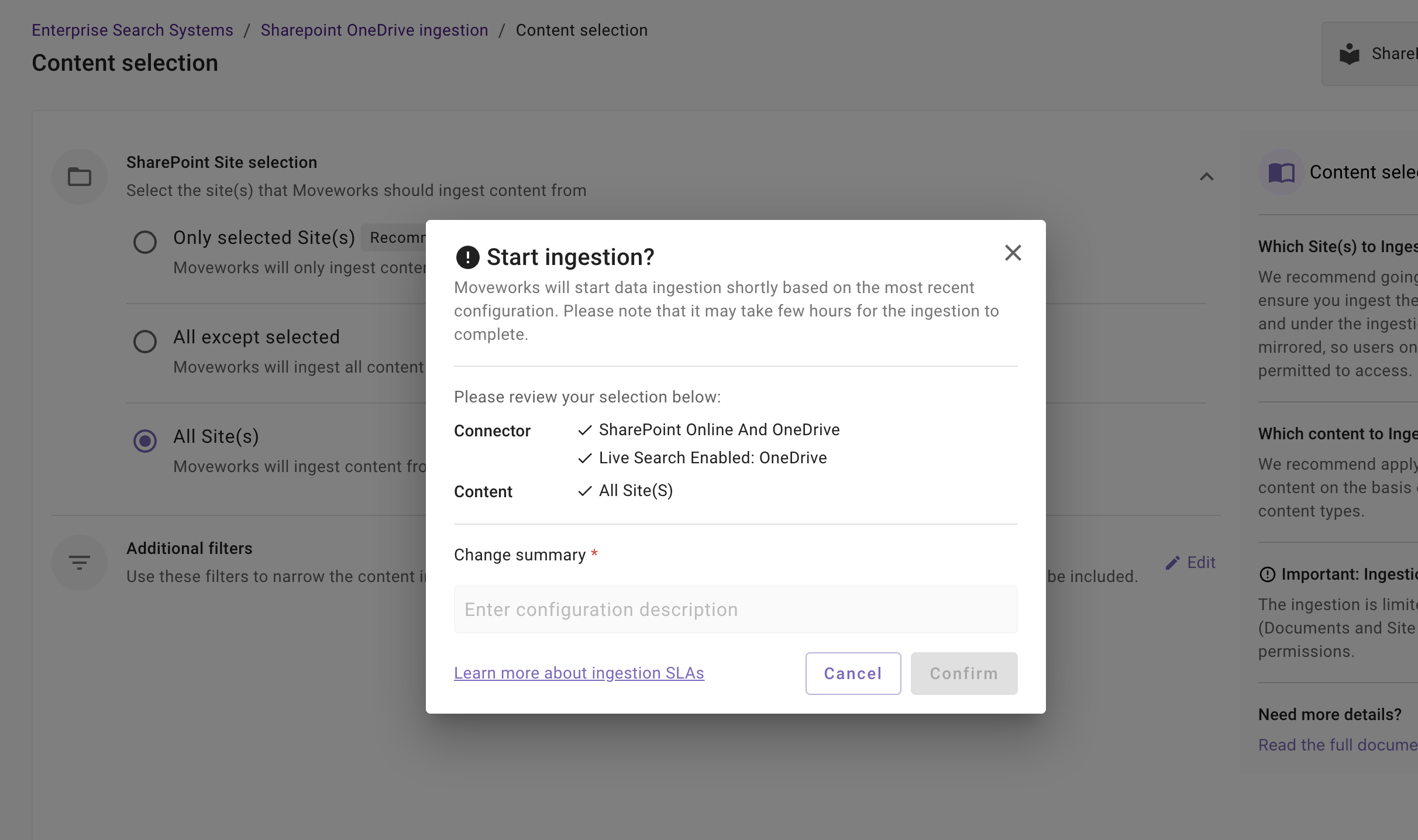
-
Click on Confirm
-
After you click on Confirm, ingestion will start shortly.
Important Note for Admins:
- It generally takes anywhere from few hours to 48 hours for the first crawl to complete depending upon the size of the data.
- You can review the status of ingestion via Data Ingestion Viewer and view ingested record in the Ingested File and Ingested Knowledge screens.
-
Troubleshooting Connector Validation Failures
Validation errors can occur when setting up a SharePoint Online or OneDrive connector. This guide helps you diagnose and resolve common issues.
Primary Validation Errors:
- "Validation failed: Invalid credentials or missing required permissions"
- "Invalid URL schema" - Base URL must use HTTPS protocol
- "Host name is not safe or valid" - The SharePoint domain cannot be resolved or is blocked
- "Failed to find connector action data" - Required configuration fields are missing or empty
Root Causes
The guide outlines potential causes by authentication method:
Server-to-Server Authentication Issues:
- Application not registered - The Azure AD application hasn't been created or registered in Microsoft Entra
- Missing API permissions - Application lacks required SharePoint permissions (
Sites.Read.AllorSites.SelectedorFiles.Read.Alletc) - Certificate issues - Invalid certificate thumbprint, expired certificate, or private key format errors
- Tenant ID mismatch - The provided Tenant ID doesn't match the SharePoint tenant
- Admin consent not granted - API permissions haven't been approved by a Global Administrator
User-Consent Authentication Issues:
- Invalid Client Secret - The client secret has expired or is incorrect
- Missing delegated permissions - OAuth application lacks either
Sites.Read.AllorFiles.Read.Allor both the delegated permissions - Refresh token expired - User needs to re-authenticate
Configuration Issues:
- Invalid tenant domain - Domain doesn't match the SharePoint site (e.g., "contoso" for contoso.sharepoint.com)
- Wrong region selected - Must choose "COMMERCIAL" for standard tenants or "GOV L4" for government clouds
- Private key format - Private key file must be in PEM format
- Empty required fields - Tenant domains list is empty or Client ID is missing
Resolution Approach
Follow these steps in sequence to diagnose and resolve validation failures:
Step 1: Verify Base Configuration
Check the fundamental connector settings:
- Confirm Tenant ID matches your Microsoft Entra tenant (found in Azure Portal → Azure Active Directory → Overview)
- Verify Tenant Domain is correct (e.g., "contoso" if your SharePoint URL is https://contoso.sharepoint.com)
- Confirm Region selection:
- "COMMERCIAL" for standard Microsoft 365 tenants
- "GOV L4" for US Government GCC High tenants
- Validate at least one tenant domain is provided
Step 2: Verify Azure AD Application Registration (Server-to-Server Auth)
For certificate-based authentication:
-
Confirm application exists:
- Navigate to Azure Portal → Azure Active Directory → App registrations
- Search for your application by Client ID
- Verify the Application ID matches the Client ID in your connector configuration
-
Check API permissions: Required Microsoft Graph permissions mentioned above - Understanding Permission Scopes required for Enterprise Search
-
Verify admin consent:
- In the application's API permissions page, check the "Status" column
- Should show "Granted for [Your Organization]"
- If not granted, click "Grant admin consent" (requires Global Administrator role)
-
Validate certificate configuration:
- Navigate to Certificates & secrets → Certificates
- Verify a certificate is uploaded and not expired
- Confirm the SHA-256 Thumbprint matches the
certificate_sha256_x5t_fingerprintin your connector config - Thumbprint format should be: uppercase hex string without colons (e.g., "A1B2C3D4E5...")
Step 3: Verify Private Key Format
The private key must be in PEM format:
-----BEGIN PRIVATE KEY-----
[Base64 encoded key data]
-----END PRIVATE KEY-----Common issues:
- Wrong format: Key must be PEM, not PFX, CER, or DER
- Missing headers: File must start with
-----BEGIN PRIVATE KEY----- - Line breaks: Ensure proper line breaks in the base64 content
- Encryption: Use unencrypted PEM files (not password-protected)
To convert from PFX to PEM:
# Extract private key from PFX file
openssl pkcs12 -in certificate.pfx -nocerts -nodes -out private-key.pemStep 4: Test OAuth Credentials (User-Consent Auth)
For OAuth2 Client Credentials authentication:
-
Verify Client ID and Secret:
- Navigate to Azure Portal → App registrations → Your App
- Confirm the Application (client) ID matches your configuration
- Check Certificates & secrets → Client secrets
- If secret is expired, generate a new one
-
Test token acquisition: Use Microsoft Graph Explorer or curl to test authentication:
curl -X POST https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/token \ -d "client_id={client-id}" \ -d "client_secret={client-secret}" \ -d "scope=https://graph.microsoft.com/.default" \ -d "grant_type=client_credentials"Should return an access token if credentials are valid.
Step 5: Verify SharePoint Access Permissions
-
Test application can access SharePoint sites:
- Use Microsoft Graph Explorer (https://developer.microsoft.com/graph/graph-explorer)
- Authenticate with your service principal or test user
- Try query:
GET https://graph.microsoft.com/v1.0/sites/{site-id}
-
Check site permissions:
- Navigate to SharePoint Admin Center → Active sites
- Select a site and check site permissions
- For app-only access, verify the application has access to required sites
Step 6: Validate URL Accessibility
The connector validates that the SharePoint instance is accessible:
-
HTTPS requirement:
- All URLs must use
https://(HTTP is rejected for security) - SharePoint Online always uses HTTPS
- All URLs must use
-
Network accessibility:
- Ensure the SharePoint domain resolves to public IPs (not internal/private addresses)
- The connector blocks connections to private IP ranges for security
-
Firewall rules:
- If using on-premise proxy, verify firewall allows outbound connections to SharePoint Online
- Check corporate proxy/firewall rules
Step 7: Advanced Troubleshooting
If issues persist after completing steps 1-6:
-
Check Azure AD audit logs:
- Azure Portal → Azure Active Directory → Audit logs
- Filter by application ID to see authentication attempts
- Look for failed sign-in events or permission errors
-
Review SharePoint audit logs:
- SharePoint Admin Center → Audit log search
- Search for activities by the service principal
- Check for access denied events
-
Validate certificate-key pair:
- Ensure the private key matches the certificate uploaded to Azure AD
- Test by using the same certificate/key pair with Azure CLI:
az login --service-principal \ -u {client-id} \ -p {path-to-pem-file} \ --tenant {tenant-id} -
Test API directly: Use the Microsoft Graph API to test access with your credentials:
- Get access token using certificate-based auth
- Test endpoints:
GET https://graph.microsoft.com/v1.0/sites?search=*(list all sites)GET https://graph.microsoft.com/v1.0/sites/{site-id}/drive/root/children(list documents)
Updated about 1 month ago