Okta Installation Guide (SAML)
SAML is not recommendedMoveworks recommends that you set up your Okta apps via OIDC. Our OIDC installation will provide a better experience. You can follow the instructions here (🔗).
This document describes the steps required to set up the Moveworks as a SAML application in Okta. Doing this will allow employees in your organization to access the Moveworks Control Center through their Okta dashboard, in the same way as they use single sign-on to access other apps they use.
Prerequisites
Making edits?Before you edit your SSO configuration, make sure you are logged into MyMoveworks. Otherwise, you will not be able to log in and update your SSO configuration details.
Okta SSO Prerequisites
- Have access to an Okta tenant
- Be an Okta administrator to that tenant
Moveworks SSO Prerequisites
-
Your Moveworks Environment should be initialized in order to continue. (Verify with your Account Team if this has been completed)
-
Note the following values.
-
data_center_domain- the data center where your organization is hosted (see table below).Data Center data_center_domain United States (default) moveworks.com Canada am-ca-central.moveworks.com EU am-eu-central.moveworks.com Australia / Asia Pacific am-ap-southeast.moveworks.com Government Secure Cloud moveworksgov.com -
subdomain- your organization's login subdomain. The value for subdomain should match yourcustomer_id, which can be verified from the General Information Page.WarningMake sure to use the unique subdomain. For example, if you're organization's login subdomain is acme.moveworks.com, then your
subdomainis acme and yourdata_center_domainis moveworks.com which is part of the US Data center. -
customer_id- The unique identifier for your organization . This is stored as Org Name under Organization Details > General Information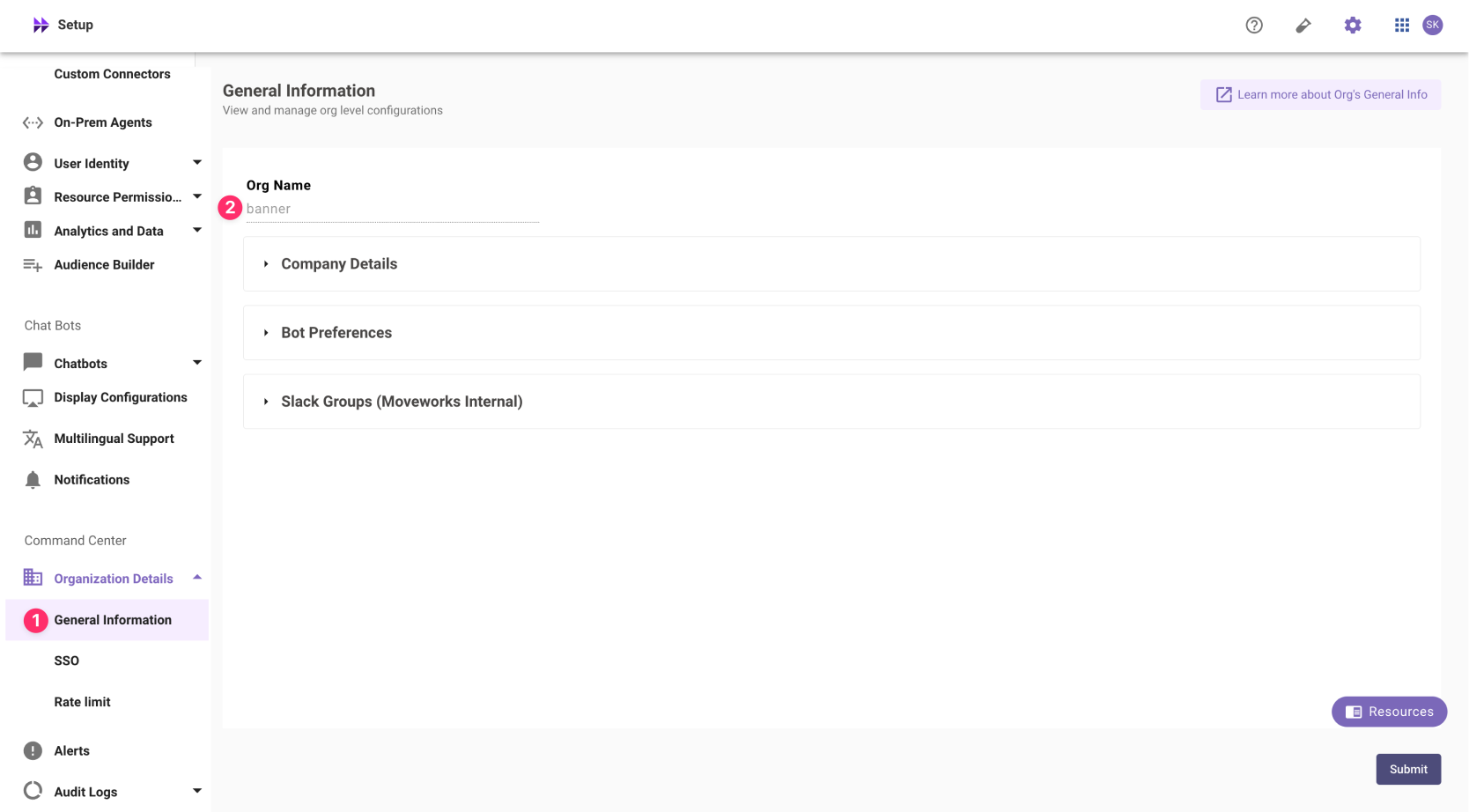 The Org name cannot be changed. Once set, the same value should be used in all cases.
The Org name cannot be changed. Once set, the same value should be used in all cases.In exceptional cases where you would like Moveworks to support your organisation with a different subdomain value. Please reach out to Moveworks Support.
-
Configuration Steps
Create SAML Application
-
Log in to your Okta org and navigate to the Admin user interface
-
Navigate to Applications > Applications.
-
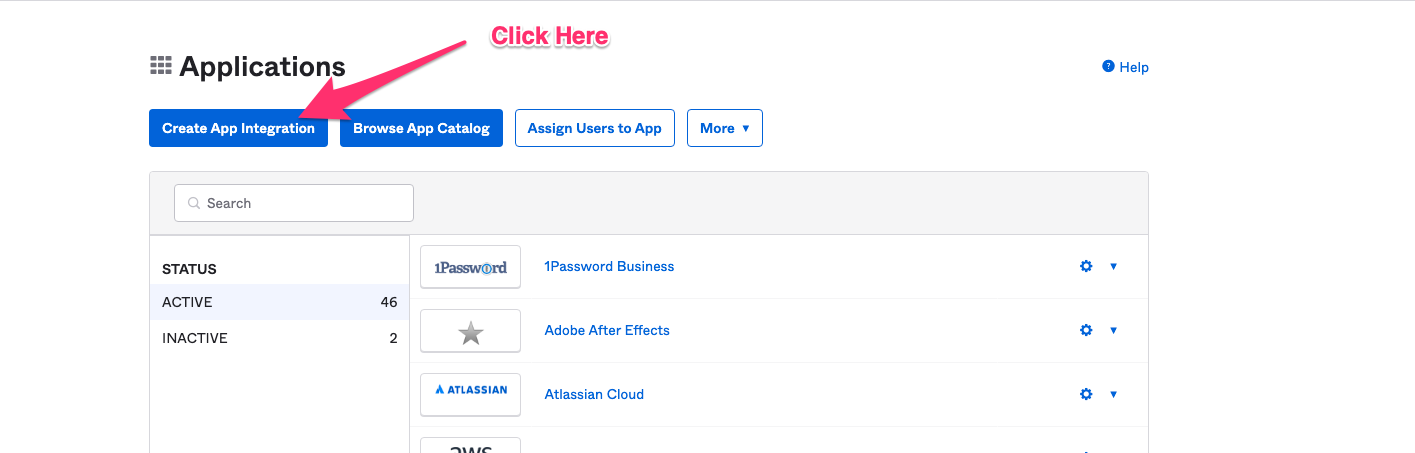
Navigate to the Applications section of Okta, and click on Create App Integration.
-
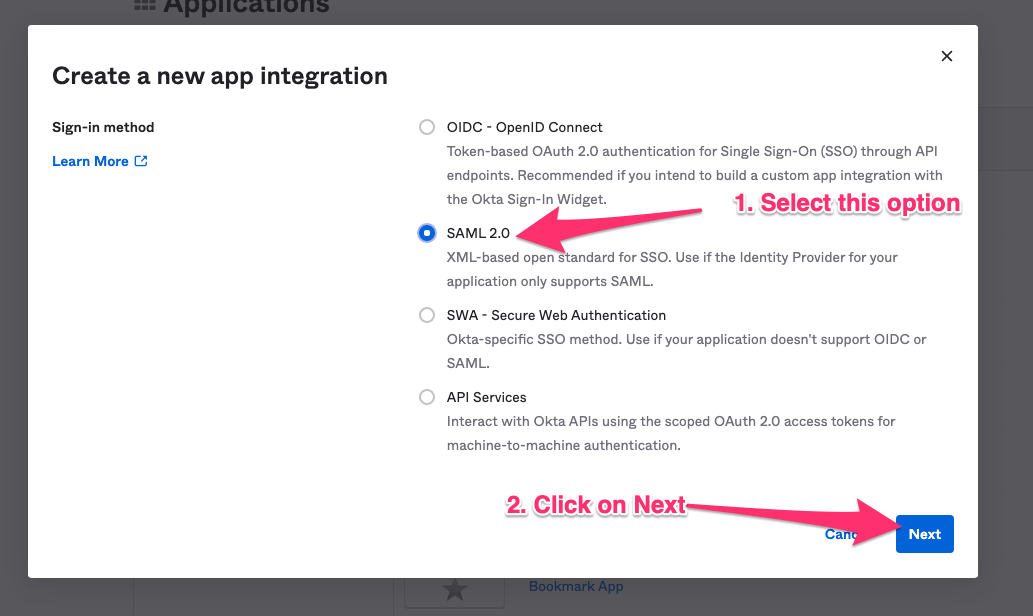
Select SAML 2.0 in the next screen.
-
Define General Settings
-
App Name:
Moveworks -
App Logo: Download the following image

-
App Visibility: Leave unchecked
-
-
Configure SAML using the values you've noted above
-
Single sign on URL:
https://{{subdomain}}.{{data_center_domain}}/login/sso/saml- e.g.
https://acme.am-eu-central.moveworks.com/login/sso/saml - Leave
Use this for Recipient URL and Destination URLselected
- e.g.
-
Audience URI:
www.moveworks.com -
Default Relay State:
customer_id -
Name ID format:
EmailAddress -
Application username:
Okta username -
Update application username on:
Create and update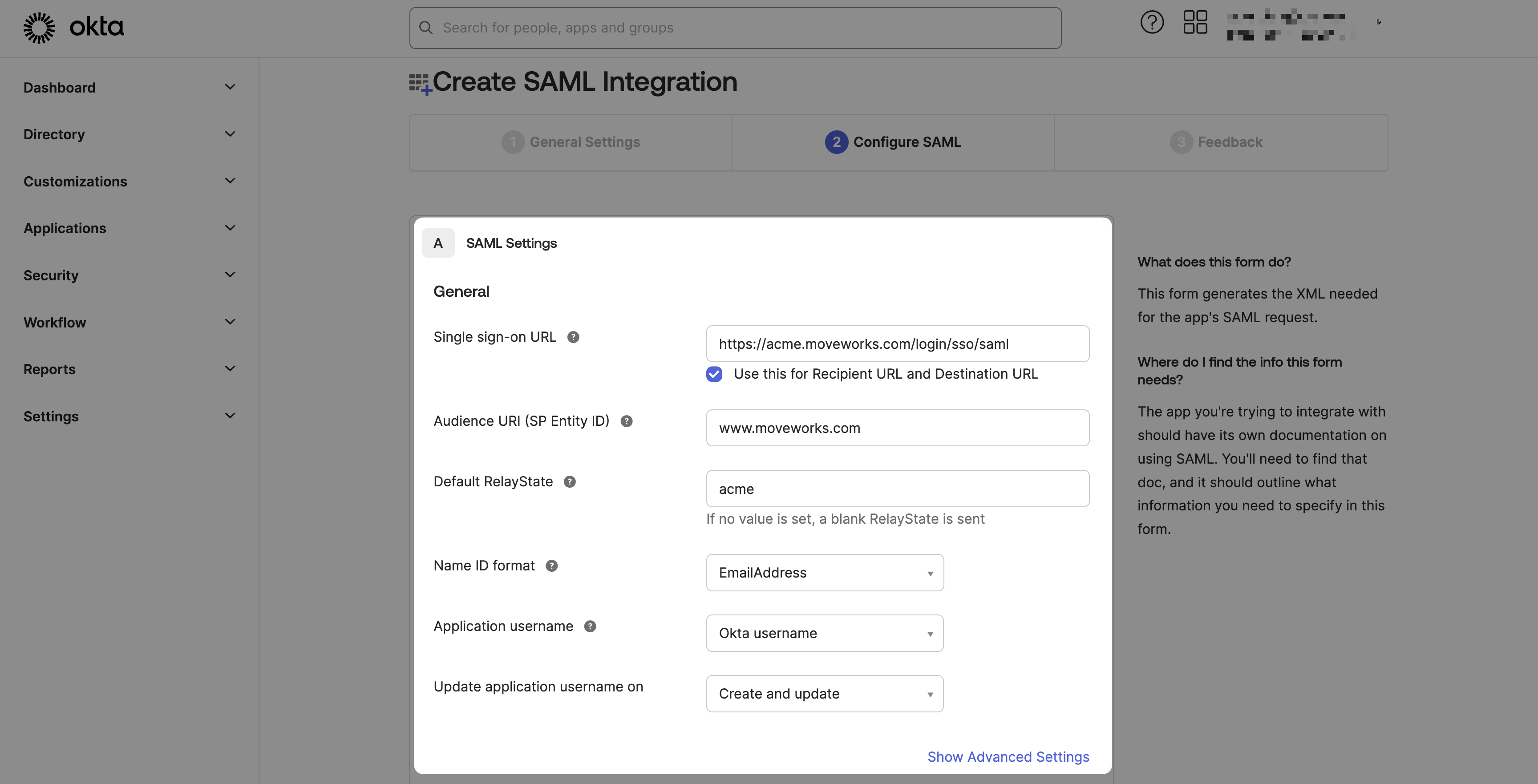
-
-
Submit Feedback & Finish
- Are you a customer or partner?
I’m an Okta customer adding an internal app - App type:
This is an internal app that we have created
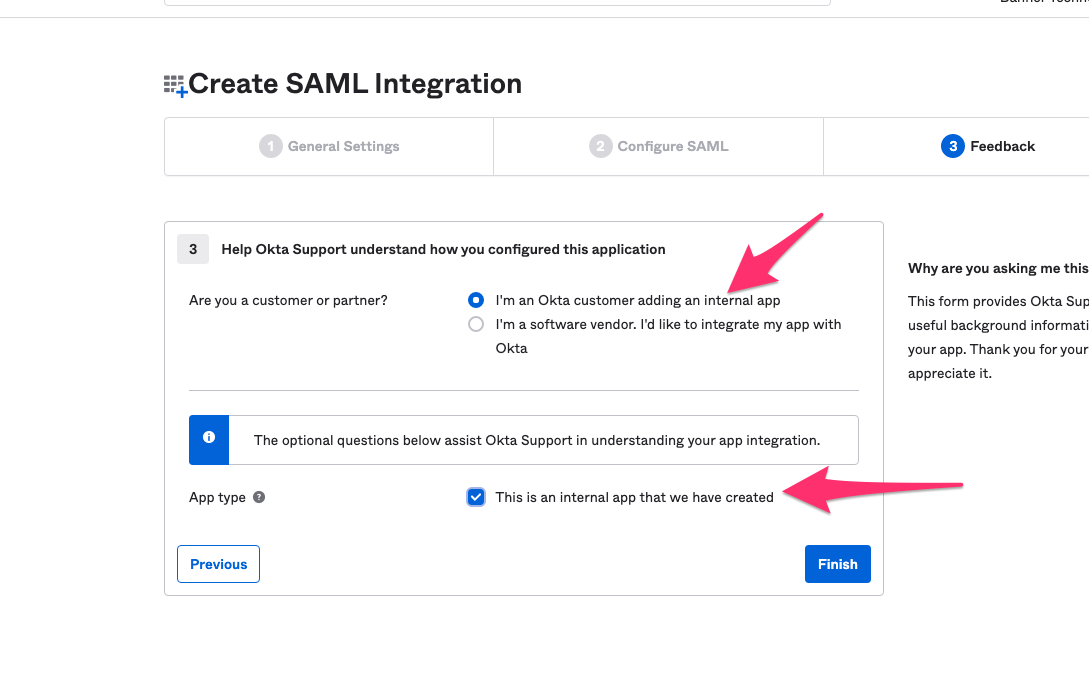
- Are you a customer or partner?
Add SAML Configuration in MyMoveworks
-
On the Sign On tab select View SAML setup instructions
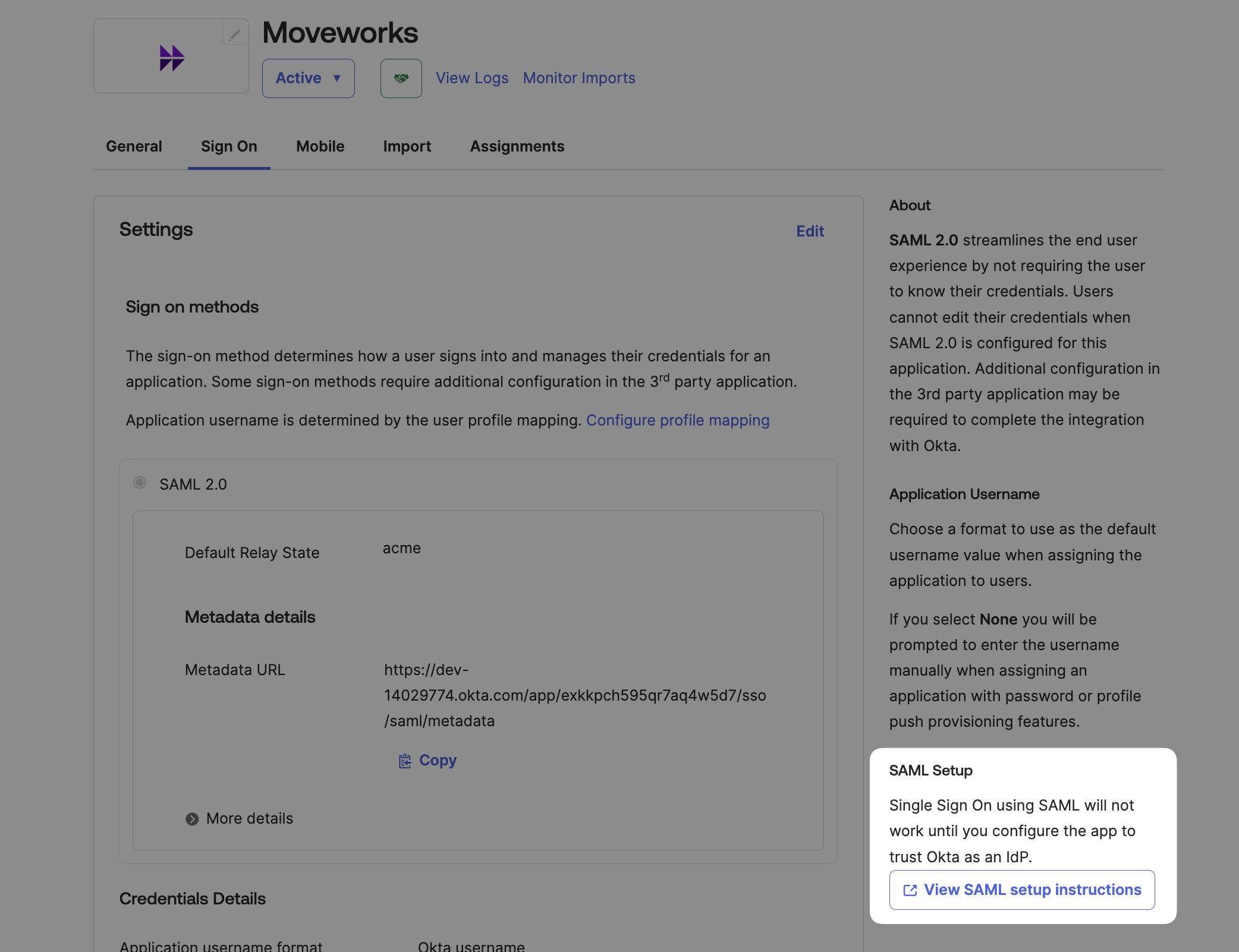
-
Copy / Download the provided information
- Identity Provider SSO URL
idp_url - Identity Provider Issuer:
idp_issuer - X.509 Certification:
x509_certificate
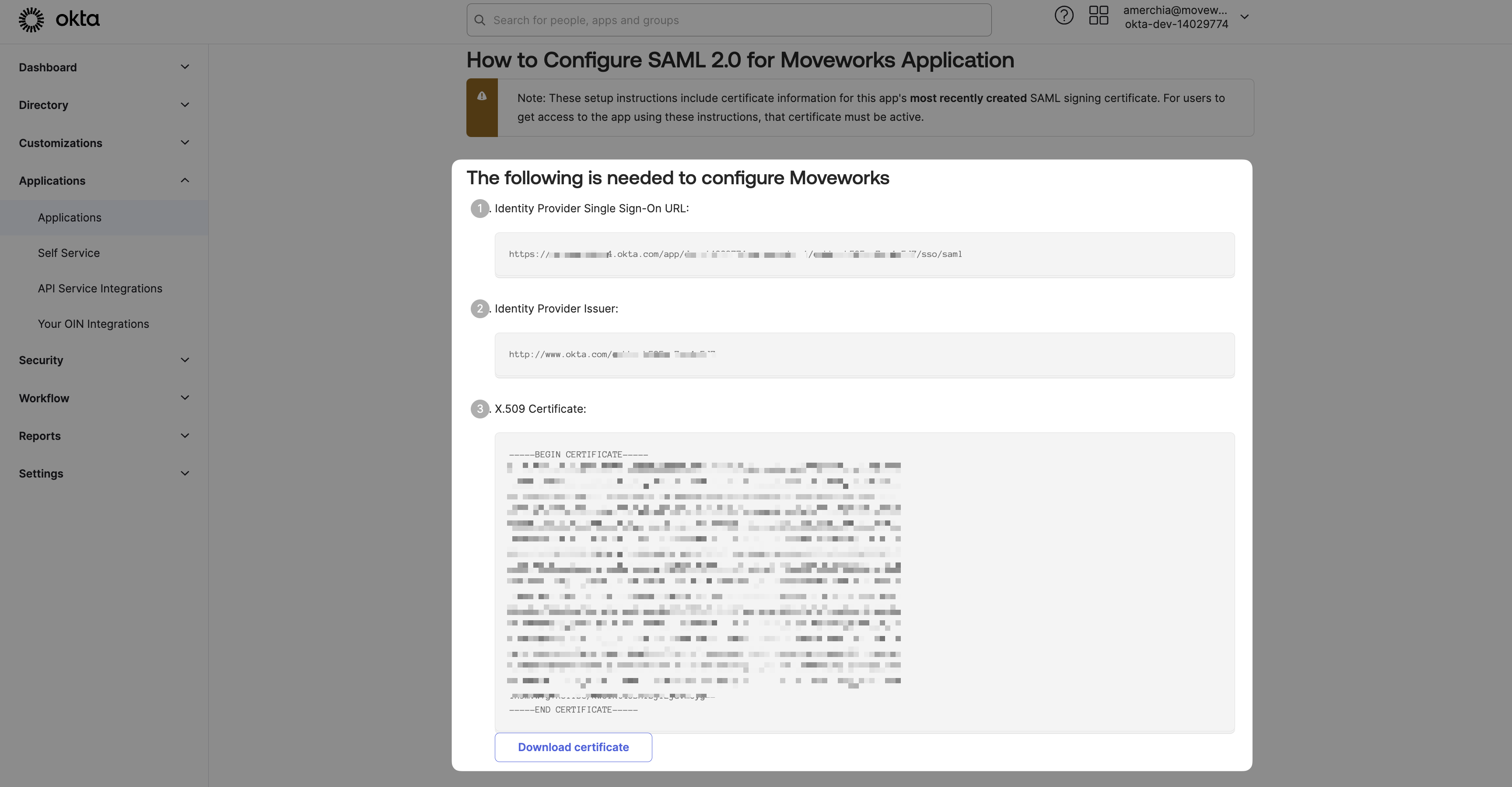
- Identity Provider SSO URL
-
Navigate to SSO Settings in MyMoveworks
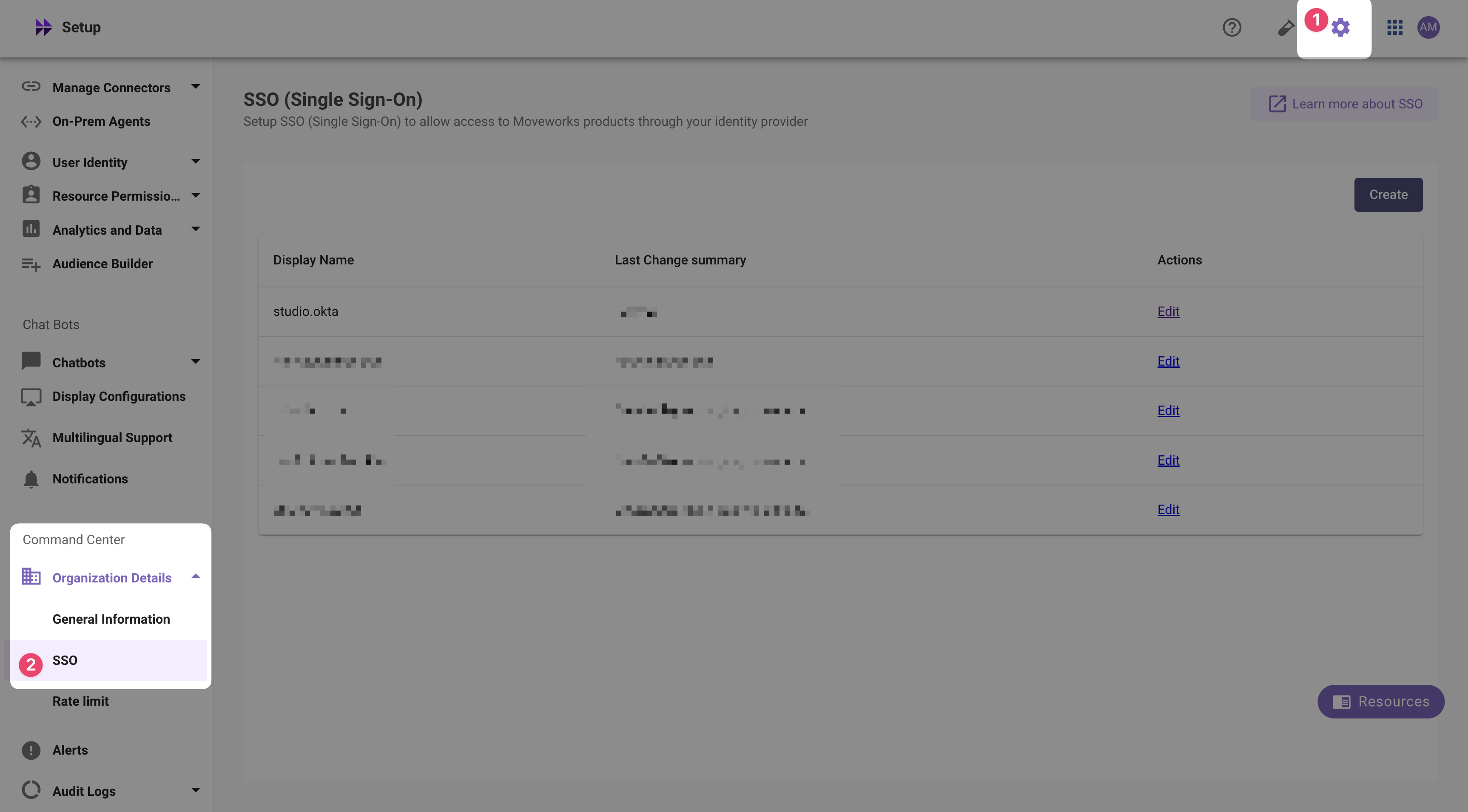
-
If you already see a
studioconfig, edit it. Otherwise, choose Create. -
Add your configuration using the values you've noted above
- Moveworks Product:
studio - Select Connector:
oktaormoveworks - Authentication Protocol:
SAML - IDP Sign On / SSO URL:
{{idp_url}}(From Step 2)- e.g.
https://acme.okta.com/app/acme_moveworks_1/d4f567gd8s9sdfgds/sso/saml
- e.g.
- IDP Issuer:
{{idp_url}}(From Step 2)- e.g.
http://www.okta.com/d4f567gd8s9sdfgds
- e.g.
- IDP Public Certificate:
x509_certificate(From Step 2)
- Moveworks Product:
-
Click Submit.
-
Wait a few minutes, then attempt to log into your instance at
https://{{subdomain}}.{{data_center_domain}}
Updated 9 months ago