Google Group (GSuite) Access Requirements
General Setup
You will need to provide the following to Moveworks.
- A Service Account JSON file associated with a Google Cloud Platform Project that has been assigned the group admin role and has access to your tenant
- Customer ID from your Google Admin Console
Please provide the Service Account JSON file to your Moveworks Customer Success team via encrypted email.
Create GCP Project & Assign APIs
Before you begin the configuration, please ensure you have the administrative privileges for the Google Cloud Platform in your organization.
- Create a GCP Project
- Start by navigating to https://console.developers.google.com/apis/dashboard in your browser.

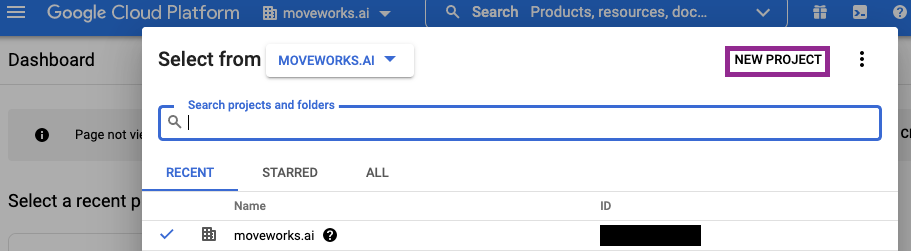
- Under your organization space, create a new project and name it “Moveworks”.
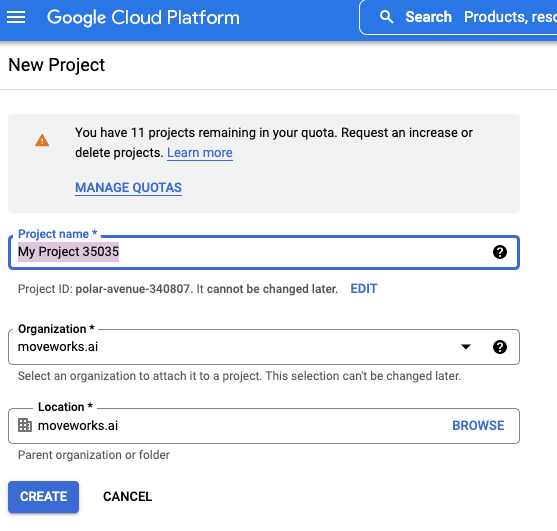
- Start by navigating to https://console.developers.google.com/apis/dashboard in your browser.
- Identify the APIs you need to enable
- Admin SDK API
- Groups Settings API
- Admin SDK Reports API
- Enable APIS for your GCP Project
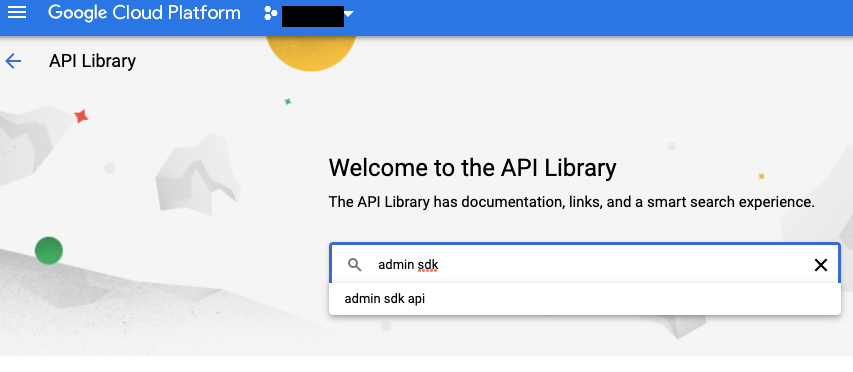
- Navigate to the API Library & Enter the name of the APIs you want to activate
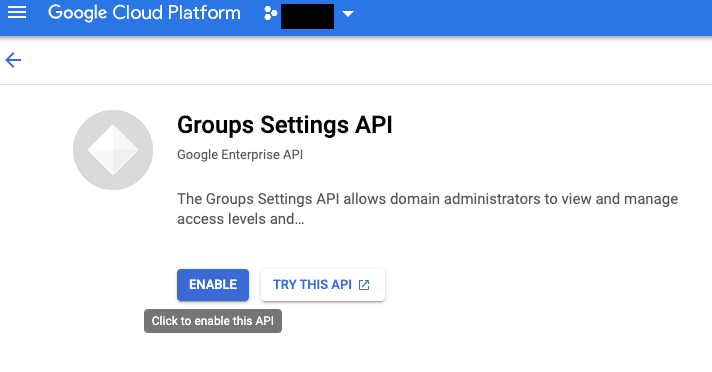
- Click Enable
- Navigate to the API Library & Enter the name of the APIs you want to activate
- Create a Service Account
- Navigate to APIs & Services > Credentials
- Select Create Credentials > Service Account

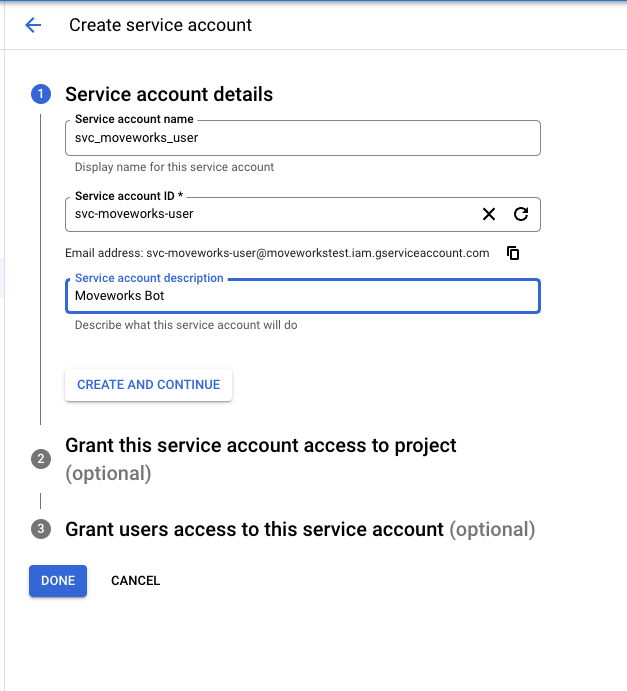
- Create the Service account by adding the name, ID and description and select Create and Continue - Note: Granting access to a project or Granting users access to this service account is optional
- Click on Actions > Manage keys
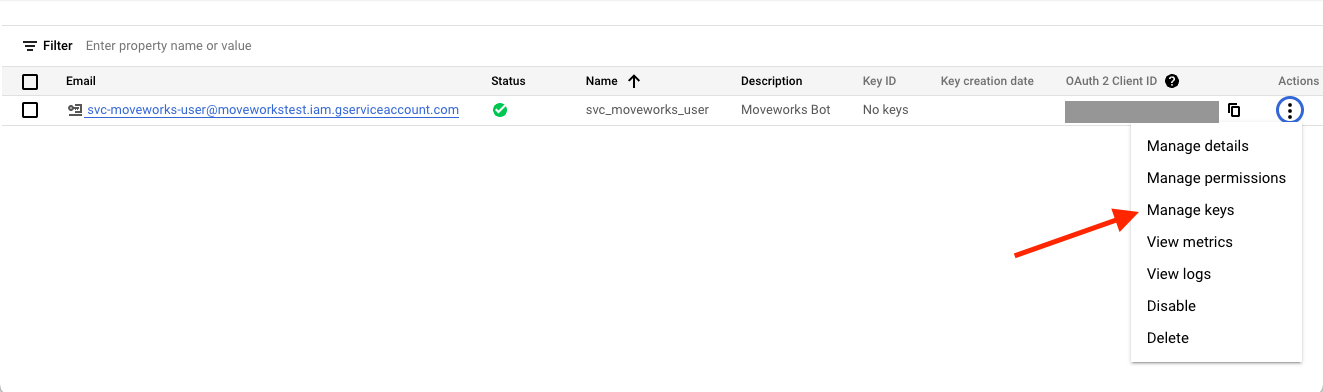
- Select Add Key > Create new key

- Select JSON as the Key type and click Create. You should see a notification that the service account JSON file has been downloaded and saved to your computer.

- Share this JSON file via secure encrypted email with your Customer Success Team
- Navigate to APIs & Services > Credentials
Fetching Customer ID:
- Sign into your Google Admin console
- In your admin console, go to Menu > Account > Account Settings > Profile
- Share the Customer ID with your Customer Success Team
Grant OAuth Scopes
This step grants the Service Account explicit permission (OAuth Scopes) to access and manage data across your domain using the enabled APIs.
Get Client ID:
- Navigate back to the Service Account details in the GCP Console (APIs & Services > Credentials).
- Find and copy the Unique ID of the Service Account (often labeled as "Client ID" in DWD steps).
- Navigate to DWD Settings:
- Sign into your Google Admin console using a Super Admin account.
- Go to Menu > Security > Access and data control > API controls.
- Under the Domain-wide Delegation pane, click Manage Domain Wide Delegation.
- Add/Edit Client Access:
- Click Add new.
- In the Client ID field, paste the Unique ID you copied from the Service Account.
- In the OAuth scopes (comma-delimited) field, enter the full, comma-separated list of required scopes enumerated in detail below.
Required Google Workspace API Scopes for Group and User Management
The following OAuth 2.0 scopes must be authorized via Domain-Wide Delegation (DWD) to ensure your Service Account can perform group creation, modification, membership changes, and read necessary directory and audit data. These scopes are mandatory for administrative actions.
Scope List Summary (Reference)
| Scope | Purpose |
|---|---|
admin.directory.group | Create, update, and delete Google Groups (Group metadata). |
admin.directory.group.member | Add, remove, and update user membership in Groups. |
apps.groups.settings | Update group configurations (e.g., who can post, moderation settings) to avoid the ACCESS_TOKEN_SCOPE_INSUFFICIENT error. |
admin.directory.user.readonly | Read user details for identity lookups. |
admin.reports.audit.readonly | Read audit logs and activity reports for compliance and troubleshooting. |
- Click Authorize.
Assigning Google Admin role to the service account:
- Sign into your Google Admin console
- In your admin console, go to Menu > Account > Admin roles
- Find the Group Admin role, select the role and click Assign admin
- Select Assign service accounts
- Enter the email address of the service account
- Click Add > Assign role
- Once complete, app should be visible in app list
You will see the Group admin role applied to the service account in your Admin audit log. Additionally, all actions taken by the Service Account will be shown in your Admin audit log.
Updated 4 months ago