How to Set Up Windows Executables as Deep Links
Admins can deploy custom protocols to have users easily run approved .exe files locally for various purposes. This guide walks through how to approach this for the Moveworks bot.
How to Deploy Custom Protocols
- Create a custom URL protocol, and then use a Group Policy Object (or another preferred method of system management) to deploy the configuration to all endpoints.
- Follow this guide or this post for more details.
- Moveworks can then present this link where applicable (see below section for use cases).
- Note: Moveworks wraps these links for tracking & analytics purposes (e.g:
https://app.moveworks.ai/?132689). This means links will immediately bounce to browser, and then redirect tocustom_protocol://, which will then link to the local.exefile.
- Note: Moveworks wraps these links for tracking & analytics purposes (e.g:
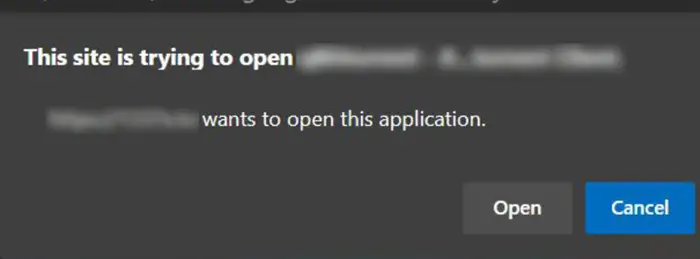
Note: Depending on your organization’s browser settings, links may result in the browser asking for permission to open the .exe.
Recommendation: You can deploy browser settings for Edge, Chrome, Firefox, etc. to auto accept your custom protocol. See this post for more details.
Moveworks Use Cases
Once deployed to your employees, these links can be used in Moveworks for the following purposes:
- Software Access: Provide a deep link to an executable file as part of the Software Access skill (with or without provisioning an IDAM group).
- Account Access: Provide a deep link to an executable file (e.g. password reset tool) when the user is required to reset an expired password or when they forgot their password.
Updated 26 days ago