Security
We understand that building trust in conversational AI technology requires a comprehensive approach to security. To ensure the trustworthiness of our solutions, we implement rigorous security measures throughout the entire product development lifecycle. This includes application security reviews, scanning capabilities (integrated in our CI/CD pipeline), penetration testing, red team exercises, bug bounty program, and as well as security operations capabilities.
Conversational AI Trustworthiness
As conversational AI becomes increasingly recognized as a tool to improve the customer and employee experience, the trustworthiness of conversational AI — specifically, ensuring that customer data is properly safeguarded — is crucial.
Since its inception, Moveworks has taken security and privacy seriously by following industry best practices and innovating in this space.
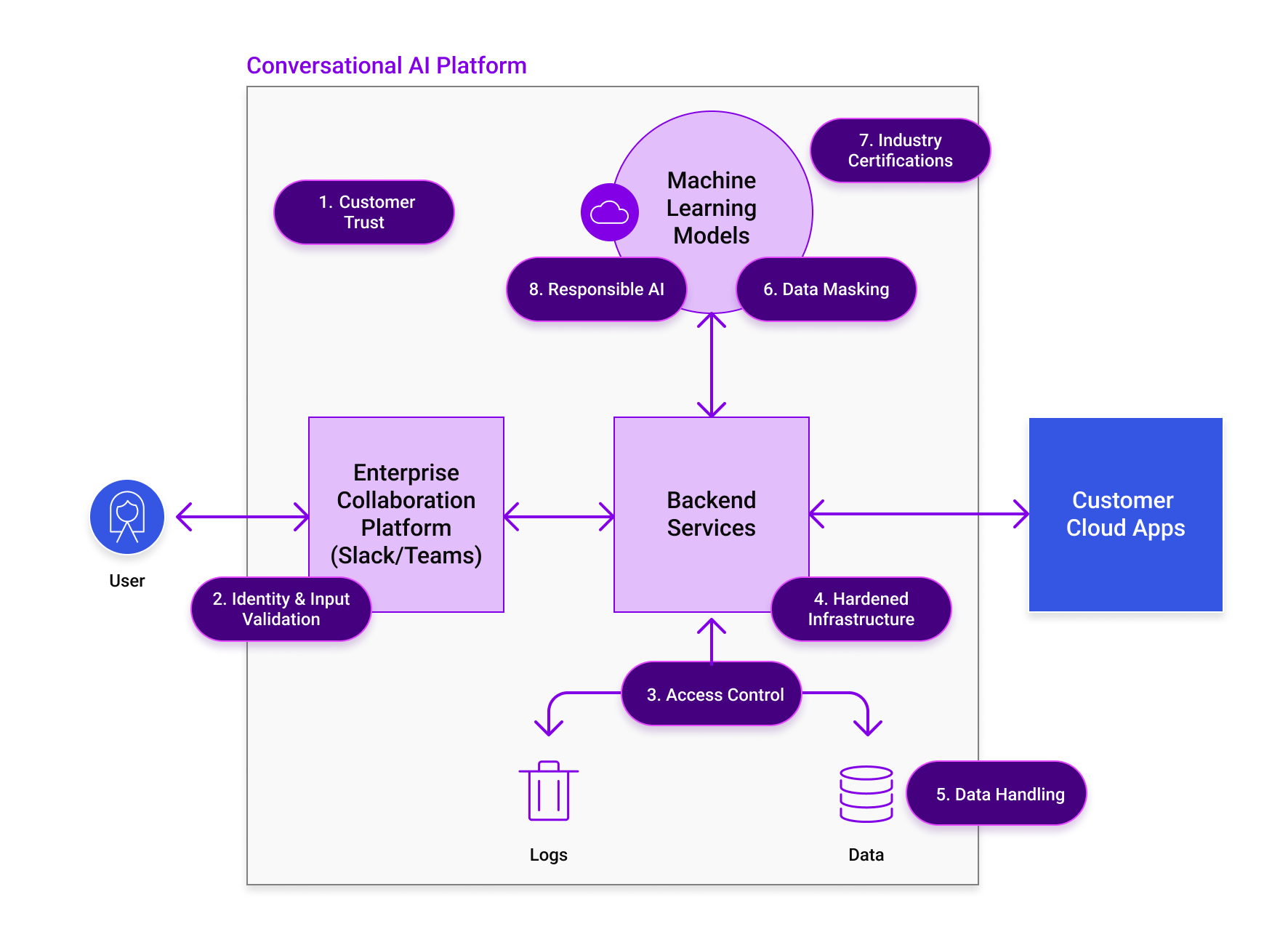
The foundations of trustworthy conversational AI
Customer Trust
A company earns customer trust by delivering on its commitments and promises. Building and maintaining trust requires well-established information security and privacy processes, mechanisms, and teams. Furthermore, there is a commitment from the executive leadership team and designated resources to promptly work on these important initiatives.
Moveworks’ Approach: Moveworks has a dedicated team of security and privacy professionals led by a Chief Information Security Officer (CISO). Moveworks has established security mechanisms & privacy processes, which are regularly updated with best-in-class practices. Moveworks also has security and privacy features built into the product to properly safeguard customer data.
Identity and Input Validation
The information exchanged between the conversational AI and the customer needs to be properly validated and the identity properly safeguarded.
Moveworks’ Approach: Moveworks validates users’ identity by integrating with enterprise collaboration platforms and identity management systems and by leveraging existing enterprise identity management systems to authenticate the user.
Access Control
Customer data should have proper access controls in place and be stored separately. The conversational AI service should only have access to the services and data needed.
Moveworks’ Approach: Access to customer data is restricted on a need-to-know basis and controlled via the least privilege mechanism. Moveworks recognizes the sensitive nature of your data, and to mitigate risk, each Moveworks customer has a logically isolated instance of our cloud services suite that is deployed and secured on AWS US West (Oregon), AWS US East (Ohio), and AWS GovCloud (US-East).
Hardened Infrastructure
Conversational AI must operate on a properly configured and secured infrastructure with secure default configurations.
Moveworks’ Approach: The Moveworks service runs as a set of containers in the Amazon Web Services (AWS) cloud with all Moveworks runtime services and runtime customer data resident in the Moveworks virtual private cloud (VPC). Moveworks maintains controls and enforces infrastructure hardening standards to ensure the confidentiality, integrity, and availability of your data. The security of the infrastructure is scanned, monitored, and audited on a regular basis.
Data Handling
Conversational AI must access and process data to service requests and generate user-specific responses. It should also have the capability to delete and mask sensitive data. A proper conversational AI relies on machine learning (ML) to improve over time, so proper privacy-enhancing technologies should be implemented. Lastly, it is important for conversational AI to ensure the data from one customer is not intertwined with another customer.
Moveworks’ Approach: Customer data is stored in a dedicated and encrypted AWS S3 bucket via AWS KMS. Data is encrypted at rest (AES-GCM 256) and in transit (TLS 1.2). All keys and credentials are encrypted and managed by AWS KMS (Rotated at least annually).
Our sample annotation data is designed to anonymize and irreversibly transform customer data, including personally identifiable information (PII), before ingesting it into our models for training.
Moveworks deletes data upon request or if your organization stops using the product (following NIST 800-88).
Data Masking
Data masking ensures that sensitive customer data is concealed from people who might need to review or access data as part of their job (such as a data annotator). A trustworthy conversational AI has this functionality to ensure that sensitive data is not exposed.
Moveworks’ Approach: Moveworks utilizes a data masking library to mask sensitive personal information such as names, emails, phone numbers, credit card numbers, etc.
Moveworks maintains strict levels of privacy by complying with industry-leading standards such as GDPR, CCPA, and ISO 27001. Customers subject to additional data privacy compliance requirements, can enter into Data Processing Addendums and Business Associate Agreements (BAA) with Moveworks, where applicable.
Industry Certification
Several industry standards and certifications highlight security and privacy. They ensure that security and privacy controls are properly implemented, including processes and mechanisms to protect its customers and their data.
Moveworks’ Approach: Moveworks’ security and privacy program has achieved the following industry certifications: SOC2 (Security, Confidentiality, Availability, and Privacy TSCs), ISO 27001, ISO 27017, ISO 27018, CSA Star Level 2 Gold, and Privacy Shield.
Responsible AI
Unbiased machine learning (ML) models require actively minimizing or eliminating potential sources of bias with respect to protected classes, including race, age, disability, religion, color, national origin, sexual orientation, gender identification, and genetic information.
Moveworks’ Approach: Moveworks samples and annotates production data without exposing any user characteristics, e.g names, photos, or other category-identifying features, to annotators within the annotation interface. When annotating the intention of a request, for example, the annotator only sees the text of the message and the organization's name.
During training and processing, Moveworks does not include protected attributes, such as gender or race, in the inputs from which the models learn to derive signals.
Handling our Customers’ Data
We understand the importance of data protection and privacy, and we are committed to safeguarding our users' data. We encrypt the data both at rest and in-transit as well as maintain strict access control mechanisms to ensure that user data is processed and stored securely. We also adhere to applicable data protection regulations (see Compliance section below), and our policies and practices ensure that we collect only necessary data for our machine learning systems to function.
How does Data Masking Work?
We use data masking as an approach to limit exposure of sensitive data by replacing or obfuscating PII data. Moveworks masks Personal Identifiable Information (PII), such as names, email addresses, credit card numbers, etc. to ensure that all data viewed by humans (for purposes of data annotation or debugging) is masked. We report all data unmasked for analytics back to the customer.
Data Minimization
We minimize the amount of data collected from the customer by allowing customers to specify data configurations, such as knowledge source and ITSM integrations. We access the minimum amount of data needed to provide services, including machine learning, analytics, and customer support. As mentioned previously, customer data is highly access-controlled and segregated, so that Moveworks systems, services, and individuals only access data on a need-to-know basis and cross-organization data access is not permitted.
Data Retention and Deletion Policy
We only retain customer data and backup copies as long as necessary to provide services. Upon request, we can delete customer data in compliance with applicable privacy laws and regulations (e.g., GDPR, CCPA). Customers can submit a request for their data to be deleted, and Moveworks will securely delete it according to the NIST 800-88 standard.
Security culture and standards compliance
As an organization that handles customer data directly, sound security practices lie at the heart of Moveworks culture. To protect the confidentiality, integrity, availability, and privacy of information under our control, Moveworks has achieved the following security and privacy certifications.
What are the Security Certifications?

- ISO 27001: Global standard for information security management systems
- ISO 27017: Code of practice for information security controls for cloud services
- ISO 27018: Code of practice for protecting personally identifiable information (PII)
- SOC 2 Type 2: Certified for security, confidentiality, availability as well as privacy TSCs
- CSA STAR Certification Level 2: Enhanced Security Controls for Cloud Service Providers
What are the Privacy Certifications?

- ISO 27701: Privacy information management standard supporting compliance with global privacy laws
- SOC 2 Type 2: Certified for security, confidentiality, availability as well as privacy TSCs
- GDPR Compliant: Protecting Data Privacy Rights
- CCPA Compliant: Safeguarding Consumer Privacy Rights
Reporting Vulnerabilities
We value the security of our products and services, and we appreciate your help in keeping them safe. If you find a vulnerability in our products or services, please report it to us through our bug bounty program.
Our bug bounty program is open to all researchers, regardless of their experience level. We offer rewards for vulnerabilities of all severity levels, and we will work with you to ensure that your report is investigated and fixed as quickly as possible.
To report a vulnerability, please visit our bug bounty program website.
When submitting a report, please include the following information:
- A brief description of the vulnerability.
- The URL of the page where the vulnerability is located.
- Any steps that are necessary to reproduce the vulnerability.
- If you have a proof-of-concept exploit, please attach it to your report.
Learn more about Security at Moveworks
For more information about Security at Moveworks, please reach out to your customer support team to get access to our Whistic profile, where you can find more of our Security documentation and certification reports.
Updated 4 months ago
